Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: Can you help me with extract fields from the f...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
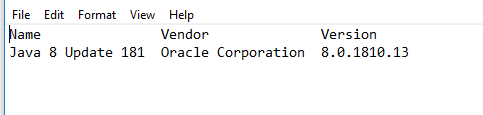
I've got wmic logfiles which look like this:
Name Vendor Version
Java 8 Update 172 (64-bit) Oracle Corporation 8.0.1720.11
Java 8 Update 181 Oracle Corporation 8.0.1810.15
Java Auto Updater Oracle Corporation 2.8.172.11
- Header is always the same
- The logs can have more than one row (some have up to 5)
- The actual data rows are always separated by two or more whitespaces
What's the proper way to extract these fields? I managed to extract the first row using the rex command — but then, all other rows are ignored. Using multiple piped rex would result in having multiple field names (Name1, Name2, Name3 etc) for each row.
| rex field=_raw "^(\w+\s+)+(?P\w+\s+\d+\s+\w+\s+\d+)\s+(?P\w+\s+\w+)\s+(?P[^ ]+)"
Thank you!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
One option would be to take a look at the multikv command, which is specifically designed for processing such data.
http://docs.splunk.com/Documentation/Splunk/latest/SearchReference/Multikv
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
One option would be to take a look at the multikv command, which is specifically designed for processing such data.
http://docs.splunk.com/Documentation/Splunk/latest/SearchReference/Multikv
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Brilliant thank you - exactly what I was looking for.