Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: Report of all available field by index and sou...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Can a report be created using metadata/any other data to list all the fields that are available by index and sourcetype?
Is there a way to create a report using metadata or any other data to list all the fields that are available by index and sourcetype.
Example
Just need to get a index, sourcetype and all available fields under them listed out as report.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@PatelAshish83 Hello,
Please try the below search:
| tstats values(sourcetype) as sourcetype where index=* OR index=_* group by index
Thanks
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Roy_9Your search does something completely different. It shows all sourcetypes from all indexes. It doesn't show any other fields.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We can 😉
But adding that to tstats won't give us much. We could add it to the original search.
I must say though that I had completely forgotten about the fieldsummary command. It's another possible approach to OP's question but unfortunately it doesn't let us split the results by any criteria (sourcetype for example).
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Extractions do not depend on index so listing them "by index" makes not much sense.
Anyway, the contents of fields.conf can be retreived by rest api /services/search/fields call. But in case of search-time extractions and calculated fields... well, there's no way to say what is "available" in any possible case. You'd have to manually parse all configuration options and decide based on this. And still you wouldn't even touch fields from automatic extractions and so on.
What you could do is list which fields are being extracted from existing events in your given timerange (something similar to what Splunk does when you click "all fields".
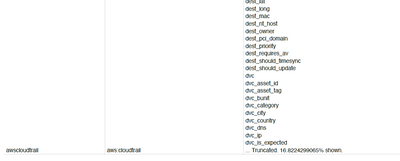
For example
<your search>
| stats dc(*) as * by index sourcetype
This will give you information about how many distinct values are there in each field. You could summarize it into a multivalued list by using untable and mvcombine if you want.