- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Average wrong box estimate- Why is my attempt wron...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
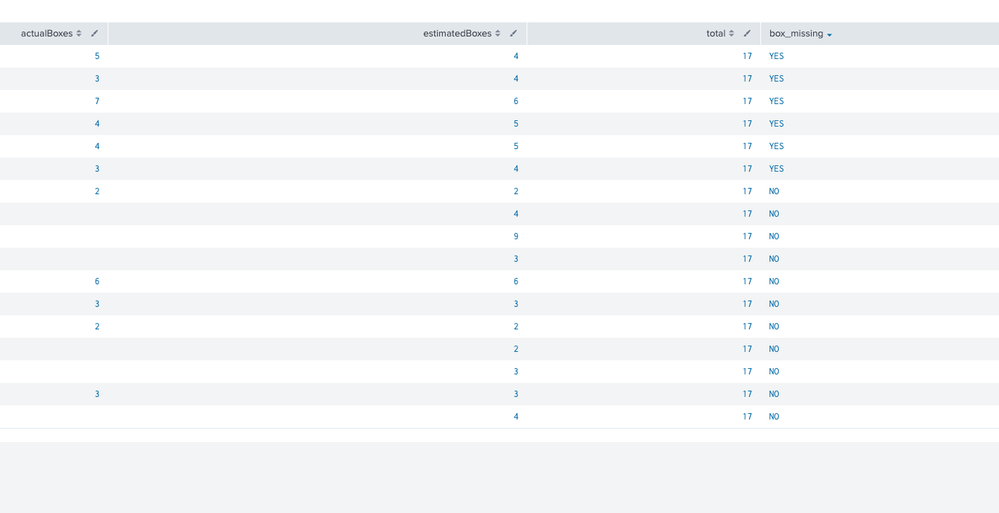
I have total 17 orders. Box Estimates is wrong 6 out of 17 orders. What is the average wrong box estimate in total?
This is my attempt who is wrong:
| spath path=data{}.actual_totes{}.finalBoxAmount output=actualBoxes
| spath path=data{}.estimated_totes{}.box output=estimatedBoxes
| eventstats count AS total
| eval box_missing=if(actualBoxes != estimatedBoxes, "YES", "NO")
| eval average= (actualBoxes - estimatedBoxes) / total * 100
| table actualBoxes estimatedBoxes total box_missing average
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
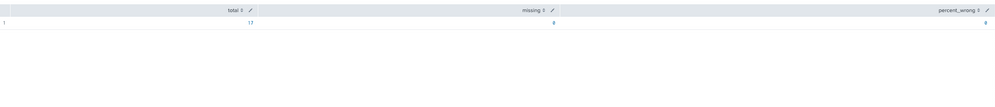
| spath path=data{}.actual_totes{}.finalBoxAmount output=actualBoxes
| spath path=data{}.estimated_totes{}.box output=estimatedBoxes
| eval box_missing=if(actualBoxes != estimatedBoxes, 1, 0)
| stats count as total sum(box_missing) as missing
| eval percent_wrong = 100*missing/total- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What events are you using?
How is it wrong?
What were you expecting?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sorry If question is not clear.
These are the data I get from my event 👇🏾👇🏾
| spath path=data{}.actual_totes{}.finalBoxAmount output=actualBoxes
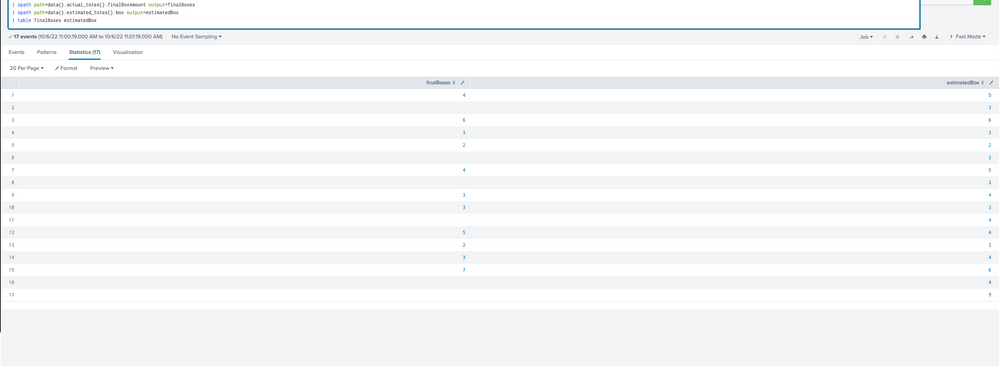
| spath path=data{}.estimated_totes{}.box output=estimatedBoxes Below splunk table image. I have estimated order was right 11 time and 6 time was wrong. I'm curious to know the percentage of incorrect box estimations overall.?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
| spath path=data{}.actual_totes{}.finalBoxAmount output=actualBoxes
| spath path=data{}.estimated_totes{}.box output=estimatedBoxes
| eval box_missing=if(actualBoxes != estimatedBoxes, 1, 0)
| stats count as total sum(box_missing) as missing
| eval percent_wrong = 100*missing/total- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I don't see any answer.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
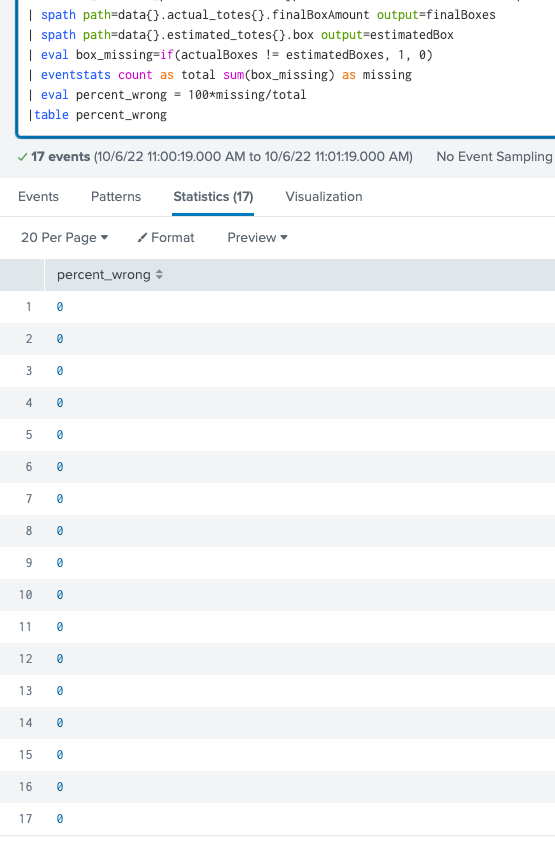
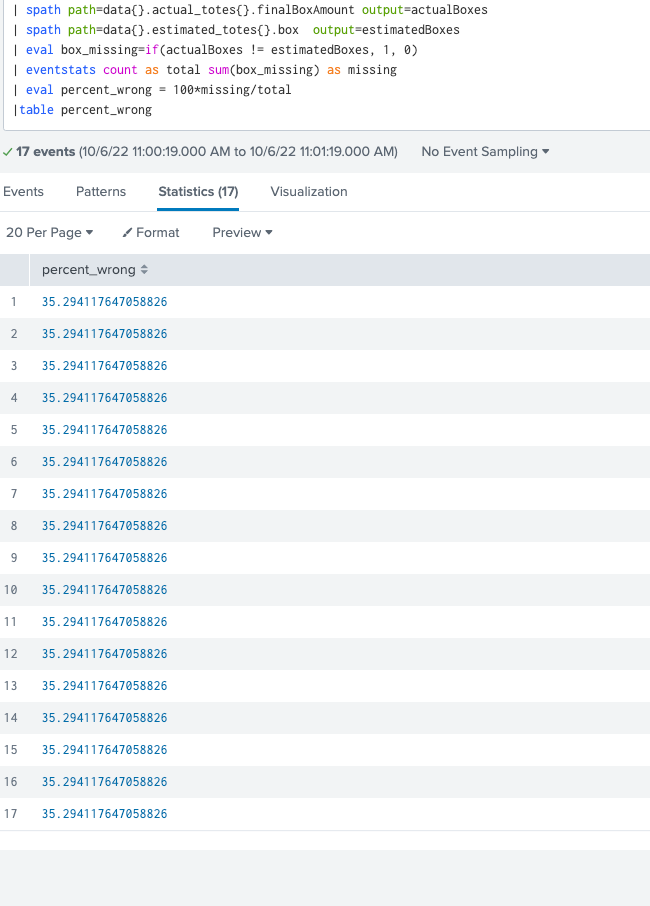
Try with eventstats so you can see which events have been included
| spath path=data{}.actual_totes{}.finalBoxAmount output=actualBoxes
| spath path=data{}.estimated_totes{}.box output=estimatedBoxes
| eval box_missing=if(actualBoxes != estimatedBoxes, 1, 0)
| eventstats count as total sum(box_missing) as missing
| eval percent_wrong = 100*missing/total- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I started learning splunk yesterday. don't know the difference between spats and evenstats. 😄
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Essentially, event stats adds the calculated values as new fields to all the events without dropping any events, whereas stats replaces all the events with a single event containing just the calculated or group by fields
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
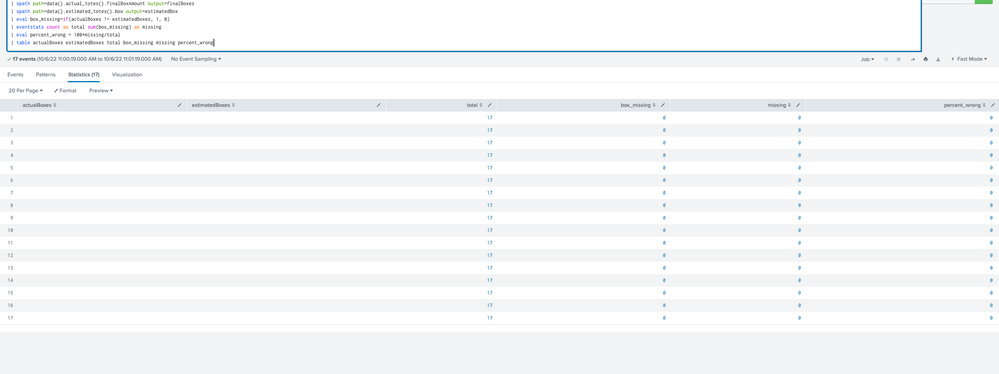
Try including the other fields
| table actualBoxes estimatedBoxes total box_missing missing percent_wrong- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
PS: I just want only TOTAL average of wrong estimate
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Your actualBoxes and estimatedBoxes have not extracted correctly (or there weren't any values for them in your events)
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How come it returns these
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
PS: Some of the actual values are null
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You have changed the names of the output fields on the spath so they no longer match the field names used in the eval - you should try and be consistent
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I am really sorry for stupid mistake 🙏🏾. Now it shows the averages but why it shows 17 rows in same result. Cant I make one column and one row
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Change the eventstats back to stats (as I explained earlier)
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you for stick with me 🙏🏾🙏🏾