Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Splunk Search
×
Join the Conversation
Without signing in, you're just watching from the sidelines. Sign in or Register to connect, share, and be part of the Splunk Community.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Average Count doesn't show?
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
dbcase
Motivator
09-02-2016
07:24 PM
Hi,
I have this query
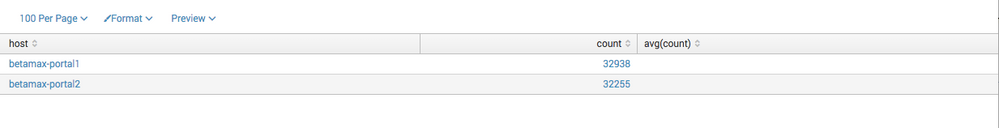
earliest=-4d index=wls OR index=main "ServletRequestImpl.java:2768" OR "rest path:/rest spec-version:2.5]] Servlet failed with Exception"|stats count avg(count) by host
And the results look like this
The count shows but no average count.... what am I missing?
1 Solution
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
somesoni2
Revered Legend
09-02-2016
08:05 PM
Give this a try.
earliest=-4d index=wls OR index=main "ServletRequestImpl.java:2768" OR "rest path:/rest spec-version:2.5]] Servlet failed with Exception"| bucket span=1d _time |stats count by _time host | stats sum(count) as count avg(count) as avg by host
Replace avg with trend line for other requirement.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
somesoni2
Revered Legend
09-02-2016
08:05 PM
Give this a try.
earliest=-4d index=wls OR index=main "ServletRequestImpl.java:2768" OR "rest path:/rest spec-version:2.5]] Servlet failed with Exception"| bucket span=1d _time |stats count by _time host | stats sum(count) as count avg(count) as avg by host
Replace avg with trend line for other requirement.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
dbcase
Motivator
09-02-2016
08:08 PM
Thanks somesoni2!!! Worked great!!!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
somesoni2
Revered Legend
09-02-2016
07:37 PM
You can't use avg(count) as the field count is not available before stats. What you want to show in avg count?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
dbcase
Motivator
09-02-2016
07:55 PM
the average by day for each host
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
dbcase
Motivator
09-02-2016
07:57 PM
I'm guessing the same applies for Trendline?
earliest=-45d index=wls OR index=main "ServletRequestImpl.java:2768" OR "rest path:/rest spec-version:2.5]] Servlet failed with Exception"|timechart span=1d count by host| trendline sma2(count) as Trend
On this query I get the same count by host but no trendline
Get Updates on the Splunk Community!
AI for AppInspect
We’re excited to announce two new updates to AppInspect designed to save you time and make the app approval ...
App Platform's 2025 Year in Review: A Year of Innovation, Growth, and Community
As we step into 2026, it’s the perfect moment to reflect on what an extraordinary year 2025 was for the Splunk ...
Operationalizing Entity Risk Score with Enterprise Security 8.3+
Overview
Enterprise Security 8.3 introduces a powerful new feature called “Entity Risk Scoring” (ERS) for ...