Join the Conversation
- Find Answers
- :
- Premium Solutions
- :
- Splunk SOAR
- :
- Phantom App for Splunk not respecting Global field...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
i have Multiple event forwardings enabled on my Phantom App for Splunk that use saved searches to trigger notable events to phantom.
I had recently we upgraded the App from ver 4.0.35 to 4.1.73.
With this upgrade all field mappings that were saved in the Event forwardings (locally) were erased. and now there are 0 fields that are mapped in the event forwardings.
Since almost all the mapped fields in each of the Event forwardings were same, i have re-mapped them manually on one of the event forwarding and while saving it i have checked the "Save Mappings" option which saves those fields in the global mappings.
but now the mappings dont work for all the event forwardings as it should (due to global mapping) but only works for the single event forwarding where the mapping is saved locally.
Troubleshooting done:
1. Tried to restore the phantom.conf file - did not work, no mapping was detected after the restore.
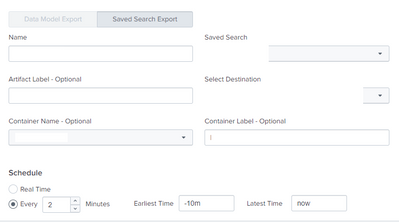
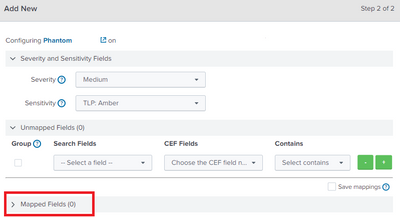
2. tried to clone the single event forwarding with locally mapped fields - did not work, as soon as i change the Saved search setting (as shown in screenshot) and save, the mapped fields turns to 0 (this is in the cloned event forwarding), as shown in the 2nd screenshot.
I really dont want to manually map the fields locally since it would result in close to 2000 fields in total (300 fields on each of the 7 event forwardings).
Any help on this issue is really appreciated.
This is the sample event forwarding config page,
the field mappings gets reset after saving the event forwarding.
I am on splunk 8.1.5
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nope, I would suggest to work with splunk support on this one.
As an immediate way out I followed the below steps:
1. Create 1 event forwarding and map all necessary fields locally in the event forwarding.
2. Clone the event forwarding of step 1. Make sure you just clone the event forwarding and do not make any changes to the cloned event forwarding from the GUI.
3. Make additional clones as required, example, if you initially had 7 event forwardings make 6 clones (1 will be the event forwarding created with all settings and mappings in step 1)
4. Login to the Splunk sh cli. Go to the add on local directory and make the necessary changes on the phantom.conf file.
This file will have all the event forwardings, you would just have to rename the search names of the clones and modify the other settings via the cli on the phantom.conf files and then push the file to the sh cluster via the deployer.
For me these steps remidiated the situation, but do make sure no one makes changes via GUI to the event forwarding config page in the future.
I think changes to field mappings are still possible (after the above steps are done) but make sure you test it. I suggest create a test event forwarding on which you can test the additional field mappings via GUI. I have not tested it though.
Hope this helps.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nope, I would suggest to work with splunk support on this one.
As an immediate way out I followed the below steps:
1. Create 1 event forwarding and map all necessary fields locally in the event forwarding.
2. Clone the event forwarding of step 1. Make sure you just clone the event forwarding and do not make any changes to the cloned event forwarding from the GUI.
3. Make additional clones as required, example, if you initially had 7 event forwardings make 6 clones (1 will be the event forwarding created with all settings and mappings in step 1)
4. Login to the Splunk sh cli. Go to the add on local directory and make the necessary changes on the phantom.conf file.
This file will have all the event forwardings, you would just have to rename the search names of the clones and modify the other settings via the cli on the phantom.conf files and then push the file to the sh cluster via the deployer.
For me these steps remidiated the situation, but do make sure no one makes changes via GUI to the event forwarding config page in the future.
I think changes to field mappings are still possible (after the above steps are done) but make sure you test it. I suggest create a test event forwarding on which you can test the additional field mappings via GUI. I have not tested it though.
Hope this helps.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for the suggested workaround this was helpful.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello @soumyasaha25 ,
I am having a similar issue and was wondering if you have figured out the root cause or a fix?