Are you a member of the Splunk Community?
- Find Answers
- :
- Premium Solutions
- :
- Security Premium Solutions
- :
- Splunk Mission Control
- :
- Incident Type and Response Task not auto assigned ...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Incident Type and Response Task not auto assigned to Incident- Is this a bug or did I not configure correctly?
One of our alerts, CSIRT - Threat_Activity_Detection, came in on 8/31 but did not auto assign the Incident Type that I created (csirt - threat_activity_detection) and therefore the Response Template I created (CSIRT – Threat Activity Detection) for that Incident did not get assigned. Is this a bug or did I not configure this properly?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is a bug on UX to provide option to update the same macro from all the incident types.
Work around for this is to update macro `mc_assign_incident_type` . The query in the macro should account for all incident types.
You can also update through the UI , like u were doing before. But the query should account for all incident types
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hey! Thank you for reaching out. I can view the incident type I created (csirt - threat_activity_detection) within Settings > Incident Types. Regarding the Incident Type Matching Macro, if I click on the link with the setting for the incident type I created ("Click here to check your macro in action"), I do get results. FYI, the value in that box is 'eval incident_type = case( severity == "medium", "CSIRT - Threat_Activity_Detection")'
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thoughts on this original issue?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yup, it's a bug! Thanks for bringing it to our attention. We'll fix it in one of our next updates.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
In addition, I see that when I create an Incident Type, it changes the 'Incident Type Matching Macro' box value of all the others to be the same as the new one I created.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@mikerennie wrote:In addition, I see that when I create an Incident Type, it changes the 'Incident Type Matching Macro' box value of all the others to be the same as the new one I created.
can you please attach a snapshot of what u see ?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sure!
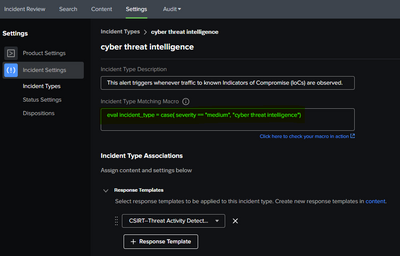
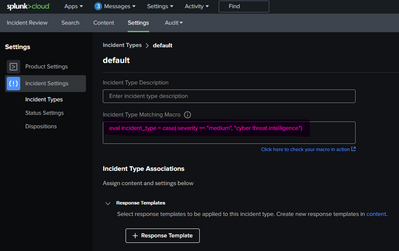
Between my two messages above, I created a new Incident Type called 'cyber threat intelligence' and created the value in the Incident Type Matching Macro box:
I now go into the other Incident Types I have (including the Default one) and it too now has the same values as the above:
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@mikerennie The Incident Type Matching Macro points to an overall macro which will determine incident type of the incident. This is to facilitate hierarchy of conditions across incident types. Therefore the query must define each incident type, not just the one being edited currently. We recognize that this is actually not intuitive in the current UI and will be working to update this. Thanks for calling it out! A sample is below:
eval incident_type=case(risk_event_count>20, "incident_type_1", urgency=="medium", "incident_type_2")Let us know if this is helpful. Happy to jump on a call to talk more!