- Find Answers
- :
- Splunk Platform
- :
- Splunk Enterprise
- :
- Not working SEDCMD. Props.conf. help
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Not working SEDCMD in my props.conf
/opt/splunk/etc/system/local/props.conf
[ActiveDirectory]
SEDCMD-mask_ms_pwd = s/(ms-Mcs-AdmPwd\s*=)\s*.*/ms-Mcs-AdmPwd=*******/
I checked it on regex101.com everything works.
wrote a line in props.conf and reloaded splunk. but still hides nothing
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You can deploy a props.conf configuration utilising “SEDCMD” and have it apply to the sourcetype “ActiveDirectory”. This means, as the data is streaming into Splunk and before it ends up on disk “indexed”, it will be anonymised. To do this we utilise the Splunk “SEDCMD”. This is much like the sed command you would find on a *nix based system. Ideally the props.conf file should be placed on a Splunk Heavy Forwarder on it’s path towards the Indexer, you could place this configuration on an indexer, but to avoid potential performance issues try use a Splunk Heavy Forwarder.
deploy-server vim /opt/splunk/etc/deployment-apps/Splunk_TA_windows
# props.conf on a HF. [ActiveDirectory] SEDCMD-anonymiseLaps = s/ms-Mcs-AdmPwd\=.*/ms-Mcs-AdmPwd=####!!!!!#####/g
save
deploy-server$ /opt/splunk/bin/splunk reload deploy-server
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You can deploy a props.conf configuration utilising “SEDCMD” and have it apply to the sourcetype “ActiveDirectory”. This means, as the data is streaming into Splunk and before it ends up on disk “indexed”, it will be anonymised. To do this we utilise the Splunk “SEDCMD”. This is much like the sed command you would find on a *nix based system. Ideally the props.conf file should be placed on a Splunk Heavy Forwarder on it’s path towards the Indexer, you could place this configuration on an indexer, but to avoid potential performance issues try use a Splunk Heavy Forwarder.
deploy-server vim /opt/splunk/etc/deployment-apps/Splunk_TA_windows
# props.conf on a HF. [ActiveDirectory] SEDCMD-anonymiseLaps = s/ms-Mcs-AdmPwd\=.*/ms-Mcs-AdmPwd=####!!!!!#####/g
save
deploy-server$ /opt/splunk/bin/splunk reload deploy-server
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It would help to see a full event as it appears as though the current SEDCMD will replace everything that follows "ms-Mcs-AdmPwd=", not just the password. Please post the event as text rather than a screenshot so we can test with it.
Recall that changes to SEDCMD affect only new data and not data that is already indexed.
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
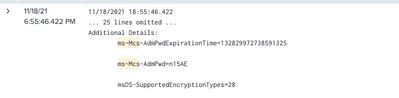
@richgalloway I know what's new. new events do not change
ms-Mcs-AdmPwd=a01LePq5
exactly what is needed. or the desired complete
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Try this regex.
SEDCMD-mask_ms_pwd = s/(ms-Mcs-AdmPwd)=(.*)/\1=******/gIf this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
not working
i changed and rebooted at 18:52. at 18:55 the event came as before
props.conf
[ActiveDirectory]
SHOULD_LINEMERGE = false
LINE_BREAKER = ([\r\n]+---splunk-admon-end-of-event---\r\n[\r\n]*)
EXTRACT-GUID = (?i)(?!=\w)(?:objectguid|guid)\s*=\s*(?<guid_lookup>[\w\-]+)
EXTRACT-SID = objectSid\s*=\s*(?<sid_lookup>\S+)
SEDCMD-mask_ms_pwd = s/(ms-Mcs-AdmPwd)=(.*)/\1=******/g
Maybe something from the other lines bothers him?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Would you mind sharing the raw event? That is what SEDCMD sees so it's what we should be working with.
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
no access to raw data. but I found a question similar to mine. and there are sources where they show an example. I drove them but also unsuccessfully
https://community.splunk.com/t5/Getting-Data-In/ms-Mcs-AdmPwd-Plaintext-in-Splunk/td-p/562704
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Where are you putting the props.conf file? It must be on the indexers and, if you have them, heavy forwarders. The instances must be restarted after making changes.
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Please share how you solved the problem so others might benefit from your experience.
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
indexer
/opt/splunk/etc/system/local/props.conf
Yes. I restarted every time I changed there
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content