Are you a member of the Splunk Community?
- Find Answers
- :
- Splunk Platform
- :
- Splunk Enterprise
- :
- How to use tstats to make a search faster (getting...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How to use tstats to make a search faster (getting errors)?
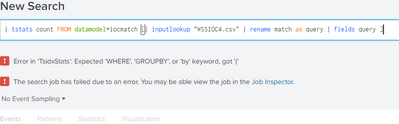
i am attempting to use tstats to make this search faster
index="wss_events" sourcetype=symantec:websecurityservice:scwss-poll
[| inputlookup "WSSIOC4.csv"
| rename match as query
| fields query ]
i get an an error that i dont understand . Can anyone tell me what i need to correct to use tstats , or am i trying to do something impossible ?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
you can not use tstats for indexed data. your indexes should be part of datamodel and datamodel should have been accelerated. read about tstats command below:
https://docs.splunk.com/Documentation/Splunk/8.0.6/SearchReference/Tstats
If this helps, give a like below.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The tstats command can be used with indexed fields.
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
i have made the index a data model , but still getting errors that i cant work out
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
When using subsearches, it's a good idea to run the subsearch by itself with | format appended as in
| inputlookup mylookup.csv | rename foo as bar | fields bar | formatThe result will show exactly what is added to the main search. If the resulting text is not valid as part of a search then the subsearch must be modified.
If this reply helps you, Karma would be appreciated.