Are you a member of the Splunk Community?
- Find Answers
- :
- Splunk Platform
- :
- Splunk Enterprise
- :
- How to use regex to view data?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How to use regex to view data?
HI
I have data that i can't access unless I use regex
but when I run the command that Splunk gives me I get the empty return.
I can use this SPL, but the performance is not good. How do I get the attribute to work for this, so I can get the performance gains.
Is it the only way I can see the data? what can i do as the performance is very bad.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
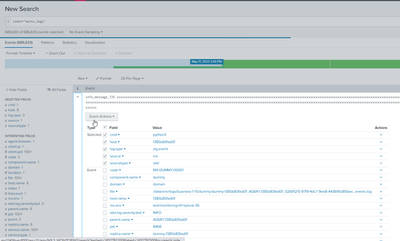
How is the field "log.type" extracted (is in raw data OR calculated OR lookup etc)? Does this work?
index="murex_logs" log.type=http
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi
This is the raw data. Its coming in via HEC.
log.type=http does not work.
However the strange this is one one environment 8.1
log.type="http" does work and 8.2.5 doesn't. However regex always works. So I looking for a way that is reliable. Its very strange.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I think its a bug in Splunk as when i downgraded to 8.1 it works
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Are you sure you're not doing something fancy with the fields? The warning suggests you're extracting a huge number of fields. That might be affecting the processing of your search.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi
THis error was not happeing in 8.2.5 only in 8.1.
I needed to add the prop in limits.conf to get rid of it.
[kv]
# Maximum number of key-value pairs that can be extracted at index time.
# Set this value to 0 to not impose any limit on indexed kv limit.
indexed_kv_limit = 0I don't know why i was getting it as i don't see over 100 fields in the data.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Have you tried single quotes instead of doubles? Single quotes tell Splunk to treat the quoted string as a field name.
index="murex_logs" 'log.type'=httpIf this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi
This did not work in 8.2.5 - thanks for you help
Rob
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
OK. That was a long-shot. Here are a couple other ideas.
Filter using where instead of in the base query. Yes, this is less efficient, but it might work.
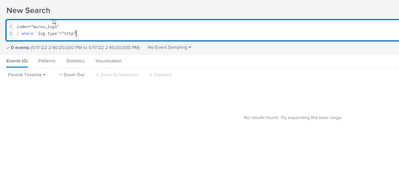
index="murex_logs"
| where 'log.type'="http"Rename the field.
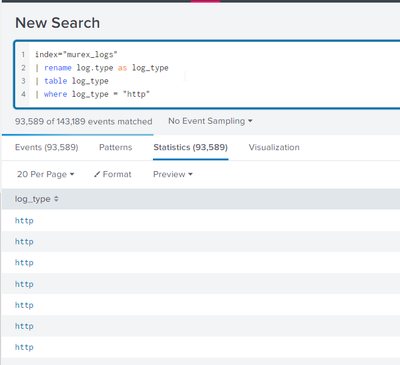
index="murex_logs"
| rename log.type as log_type
| where log_type="http"If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
hi
So this will only work if I put a table command into it, but i think the table command will slow it down.
As you can see this does not work.
Do you think it's a bug in Splunk or because i am getting in HEC OT data?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
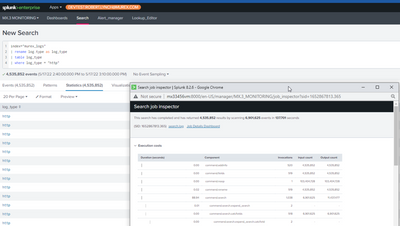
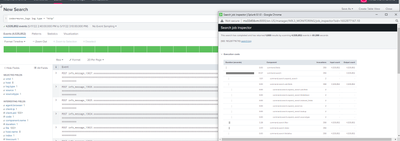
Also to add adding the table command slowed the search down big time from 137 seconds to 61 seconds.
So i can't use the table command to fix this
The first screenshot is from 8.2.5
The second screenshot is from 8.1
do you think i should make a bug to Spunk or do you have a few more ideas, also thanks again for all the efforts 🙂