Are you a member of the Splunk Community?
- Find Answers
- :
- Premium Solutions
- :
- Splunk Enterprise Security
- :
- Re: no expected fields in sourcetype
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
no expected fields in sourcetype
Hello all!
resently i downloaded Check Point App for Splunk. I configured in input.conf in order to force all Chechpoint devices send their logs to sourcetype cp_log:
[udp://
sourcetype = cp_log
now i can see all necesary logs in this sourcetype, but if i look at soucetype settings - i can see that there should be many various fields. but i cannot see these fiedls while i perform search. No necesary fields - no output on my Check Point App for Splunk. how to get these fields? or should i extract every field mannually?
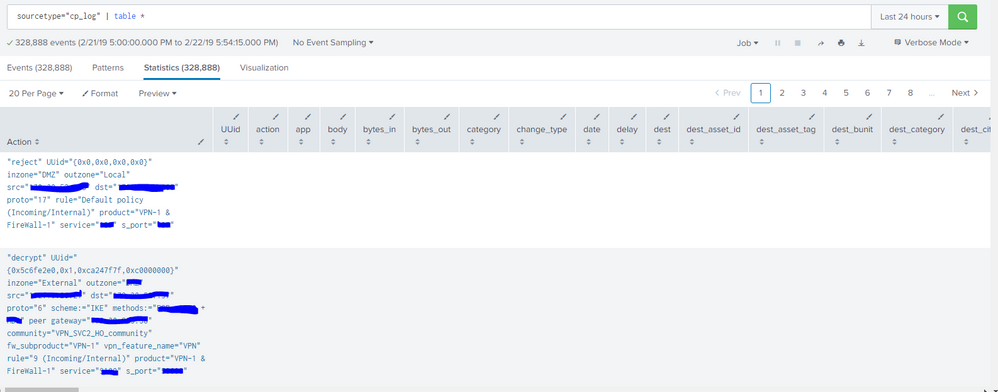
But search " sourcetype="cp_log" | table *" returns table with fields that i need, but all of them are empty. Only field "Action" contain whole log text(look at attached picture)
APP link - https://splunkbase.splunk.com/app/4293/#/overview/
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you for your responce... but no... "All fields" - is already selected... (it seem my case is similar to the next https://answers.splunk.com/answers/206812/splunk-add-on-for-cisco-wsa-not-extracting-fields.html)
screenshot as an answer to your question is below: