Are you a member of the Splunk Community?
- Find Answers
- :
- Premium Solutions
- :
- Splunk Enterprise Security
- :
- Why aren't my IDS logs populating the Intrusion De...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
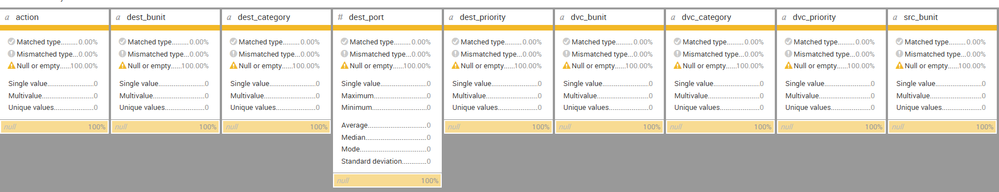
I am using Splunk ES and trying to match my IDS logs to the Intrusion Detection data model. I thought I did all preparatory steps required but when clicking in the ES app Search > Datasets > Intrusion Detection > IDS Attacks > Summarize Fields nearly all the of the fields are listed as "null or empty" and the few that are populated contain "unknown" in them.
Here is what I have done so far:
- Created event type search to identify the logs and tag them as "ids" and "attack" per CIM docs (shared globally)
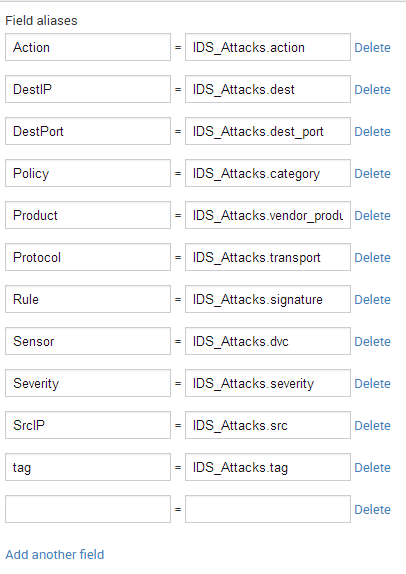
- Created field aliases (shared globally) as most of my existing logs are named something other than the expected datamodel field name
3. Validating the data per step 6A
4. End result mostly null or unknown
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
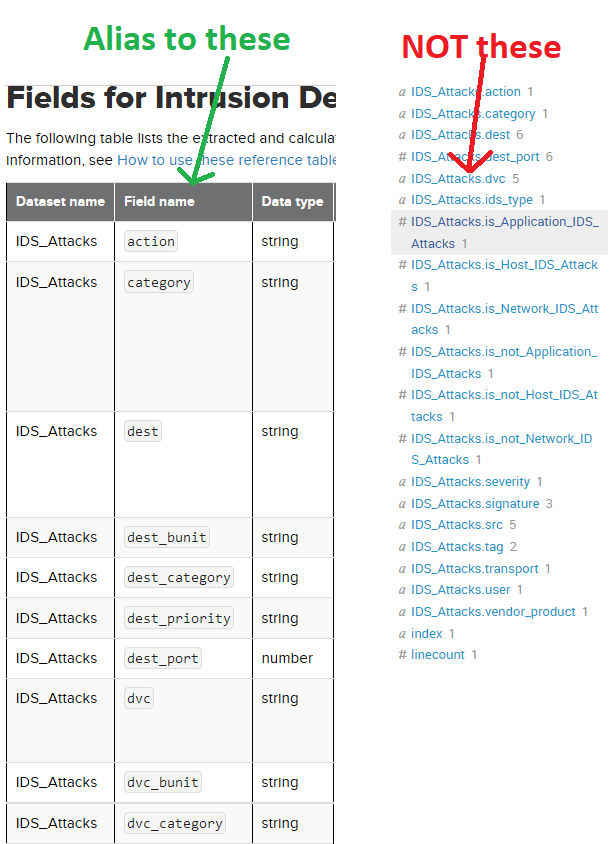
The way to fix this is I had to rename the field aliases to the data model field name that's listed in the docs (go figure) rather than what was showing up in search (see below)
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The way to fix this is I had to rename the field aliases to the data model field name that's listed in the docs (go figure) rather than what was showing up in search (see below)