- Splunk Answers
- :
- Splunk Premium Solutions
- :
- Security Premium Solutions
- :
- Splunk Enterprise Security
- :
- Re: Threat Intelligence Weekly Statistics
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Threat Intelligence Weekly Statistics
I have been trying to get some statistics around the Threat Intel that is being pushed into the the comes into Splunk this is for some trend analysis around how many indicators we see on a weekly basis. It needs to be a split of threat intel count collected over a 7 day period.
I have tried using the timechart command with spans to split the number of events counted per-day and the time picker set to 7 days. However this does not work as expected.
|`email_intel` | `http_intel` | `ip_intel`
| convert ctime(time) as _time
|search threat_key="****"
|timechart span=24h count
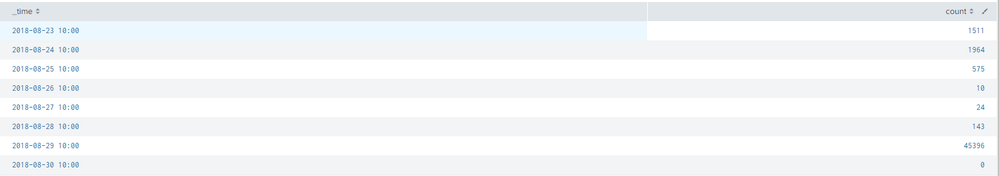
See output
This output is not correct the time stamp always shows a fixed hour, even though the actual _time field shows the correct time the intel was ingested. I have also tried different iterations to solve the same problem using the bin and the stats command
|`email_intel` | `http_intel` | `ip_intel`
|search threat_key="****"
| convert ctime(time) as _time
| bin span=12h _time
| stats count by _time
Is there a better way of doing this? Would appreciate any help
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
what is it that you want as output? possible to provide a mockup?
As such both timechart and stats are working as expected. If you aggregate counts over a span, the resultant counts will always be accumulated. This is true of any application and not just splunk.
What would be your expected output?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for your reply @Sukisen1981 . I need to see how many threat indicators have been ingested per day, so ideally if i set the timepicker to 7 days i want to see one time entry for every day of the week and the accumulated count of the indicators that were ingested on that day. The output screenshot that you see is how i want it structured but currently the count of indicators per-day is not accurate.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
hmm your screen shot is exactly the output you should receive when running your query, so i am confused a bit.
run this querybuild on _audit index, this should run as it is for you, choose last 24 hours as default.
index="_audit" | convert ctime(time) as _time|eval x=_indextime | eval x=strftime(x,"%m-%d-%y %H:%M:%S") | timechart span=5min count,values(x) |rename values(x) as detail_time|fields _time,detail_time,count
Is this something like what you want?