Join the Conversation
- Find Answers
- :
- Premium Solutions
- :
- Splunk Enterprise Security
- :
- How to move multivalue fields as separate columns?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi, I have the following case which I can't get around.
My search returns something like this:
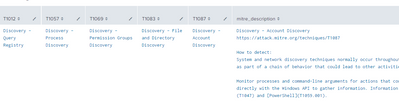
In order to help security analysts with some useful information, from a lookup we are adding MITRE technique ID and some useful information about how to detect this particular technique.
What I wanted to do is to move the multivalue fields from mitre_technique_id column as the separate columns named exactly like the MITRE ID, and in that column I wanted to include the information about the detection tips for that technique.
I was trying something with foreach, transpose, mvexpand but with no good results.
Does anyone knows how to achieve it? The end result would look like this:
Thanks in advance!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
| streamstats count as row
| eval iddetect=mvzip(mitre_technique_id,mitre_detection,"|")
| mvexpand iddetect
| rex field=iddetect "(?<_name>[^\|]+)\|(?<_value>.+)"
| eval {_name}=_value
| fields - iddetect mitre_technique_id mitre_detection
| stats values(*) as * by row
| fields - row- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Give this a try
YOur current search giving field host, dest, user, mitre_technique_id mitre_detection
| eval iddetect=mvzip(mitre_technique_id,mitre_detection,"|")
| mvexpand iddetect
| rex field=iddetect "(?<mitre_technique_id>[^\|]+)\|(?<mitre_detection>.+)"
| fields - iddetect
| eval common_key=host."##".dest."##".user
| xyseries common_key mitre_technique_id mitre_detection
| rex field=common_key "(?<host>[^#]+)##(?<dest>.+)##(?<user>.+)"
| fields - common_key
| table host dest user *- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
| streamstats count as row
| eval iddetect=mvzip(mitre_technique_id,mitre_detection,"|")
| mvexpand iddetect
| rex field=iddetect "(?<_name>[^\|]+)\|(?<_value>.+)"
| eval {_name}=_value
| fields - iddetect mitre_technique_id mitre_detection
| stats values(*) as * by row
| fields - row- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Solved by adding (?s) in front of the regex.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks, I see the light in the tunnel 🙂
How to modify that regex so it captures remaining lines of the paragraph?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Try this
| rex field=iddetect "(?ms)(?<_name>[^\|]+)\|(?<_value>.+)"