Are you a member of the Splunk Community?
- Find Answers
- :
- Premium Solutions
- :
- Splunk Enterprise Security
- :
- How to create notable events with search?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have Power-user access only.
I have a Splunk query and I enabled an alert as a Notable Event. And I also received the notable events in ES --> Incident Review.
But I am not getting the Search query's result in my notable events. I am only getting the Alert name.
Search results of the query are not received in the notable events.
I want to get all the query's search results in the notable events. Please help.
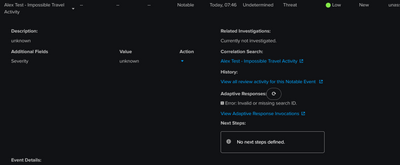
Received Notable Event with no information
Actual Query's Search Result
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If you go to Edit Correlation Search in ES, and then click "Notable" at the bottom, you can add your description that you would like to have. It supports variables.
What fields are you wanting to show up in the Additional Fields section? Those fields can be added in the Incident Review Settings under Configure in the ES navigation row.
Under " Incident Review - Event Attributes" is there you would map those fields you want to show up.
You also have the option to rename some of the fields in your original query to map to some of those labels.
I hope this helps!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If you go to Edit Correlation Search in ES, and then click "Notable" at the bottom, you can add your description that you would like to have. It supports variables.
What fields are you wanting to show up in the Additional Fields section? Those fields can be added in the Incident Review Settings under Configure in the ES navigation row.
Under " Incident Review - Event Attributes" is there you would map those fields you want to show up.
You also have the option to rename some of the fields in your original query to map to some of those labels.
I hope this helps!