Are you a member of the Splunk Community?
- Find Answers
- :
- Premium Solutions
- :
- Splunk Enterprise Security
- :
- How does Splunk define and assign urgency in Splun...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How does Splunk define and assign urgency in Splunk Enterprise Security?
Hello everyone
I'm using Splunk Enterprise Security, and at the first sight, I saw urgency which includes: "critical, high, medium, law, info"
How are these actions divided to these groups? Is there any code behind it as the code in investigations which we could change them manually?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You wrote
"but...
to clear my meaning, my exact question is how it can understand these priority and severity?
for example there is a medium risk attack, and splunk understand it as a medium...right? how they do it exactly?
or maybe it is critical but they said high, we can change them manually! so there must be something, or some code behind it! to define them as a priority and severity!"
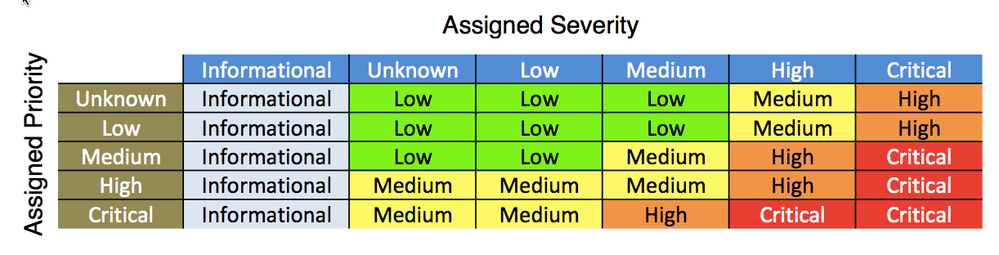
Splunk assigns ugency by mapping the assigned severity to the assigned priority of the asset for the various correlation searches.
It is important to check the chart given in the answer above by koshyk . I found most of our assets were classified as unknown therefore lowering the urgency of the alert.
What we did to fix this situation was to change the columns so that ugency matched the assigned severity. This may not have been the best solution but it solved our issue. We were then easily able to map the urgency on the incident review dashboard to the expected severity in the correlation search as it no longer considered the asset in making the determination.
Hope this helps.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
hi,
Urgency is a combination of
1. Priority of the Device when you build your assets (You can fetch from external sources (eg cmdb) or assign manually. Doc link)
2. Severity of the use-case ( You define them when you write the use case/co-relation search)
Matrix attached below. Further details of how it can be done etc is show here
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you a lot koshyk (@koshyk)
but...
to clear my meaning, my exact question is how it can understand these priority and severity?
for example there is a medium risk attack, and splunk understand it as a medium...right? how they do it exactly?
or maybe it is critical but they said high, we can change them manually! so there must be something, or some code behind it! to define them as a priority and severity!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
hi, I've added bit more description to my answer on how to assign them. If you think it is ok, please mark it as answer. cheers
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Will the search command help you?
From Incident Review dashboard, click Job -> Inspect Job on the timeline chart
A new window opens. Click search.log link at the top
Text search for 'SearchParser - AFTER EXPANDING MACROS' and you will see the SPL search command there.
Copy the command and run it in the Search and you will see how these data computed
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Documentation of the above can be found here: http://docs.splunk.com/Documentation/ES/4.5.1/User/NotableEvents#How_urgency_is_assigned_to_notable_...