- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
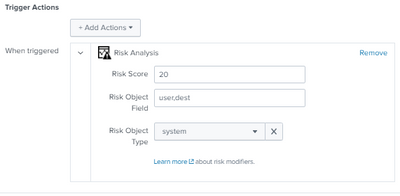
How to assign multiple risk object fields and object types in Risk analysis response action. I know it's possible from search using appendpipe and sendalert but we want this to be added from the response action.
Example as below:
Risk Score - 20
Risk Object Field - user, ip, host
Risk Object Type - System, user
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
In your correlation search create a fields risk_object and risk_object_type containing your values and have one row per risk entry you want to create. You can also give each row a different risk score if you want to. This example shows how you can use those fields.
| makeresults
| fields - _time
| eval risk_object=split("vamshikn72:user,10.10.13.11:system,machine1:system", ",")
| mvexpand risk_object
| rex field=risk_object "(?<risk_object>[^:]*):(?<risk_object_type>.*)"
| eval risk_score=20In the configuration dialog, just leave the risk object and type fields blank. If you include a score field in the row, it will use that instead.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
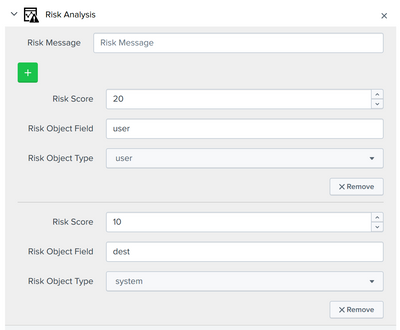
The easyest way is to upgrade your Enterprise Security to 6.4, which has the option to add multiple risk analysis to the same result.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks @MaverickT. We came to know about this later and asked our admins to upgrade.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
In your correlation search create a fields risk_object and risk_object_type containing your values and have one row per risk entry you want to create. You can also give each row a different risk score if you want to. This example shows how you can use those fields.
| makeresults
| fields - _time
| eval risk_object=split("vamshikn72:user,10.10.13.11:system,machine1:system", ",")
| mvexpand risk_object
| rex field=risk_object "(?<risk_object>[^:]*):(?<risk_object_type>.*)"
| eval risk_score=20In the configuration dialog, just leave the risk object and type fields blank. If you include a score field in the row, it will use that instead.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @bowesmana, Passing blank values in the response action and adding scores to the eval helped me a lot. Thanks for your quick help.
Search example I used:
| makeresults
| eval field_user="noob", field_ip="8.8.8.8", field_host="machine"
| eval risk_object=if(isnotnull(field_host),field_host,null()),risk_object_type=if(isnotnull(field_host),"system",null())
| appendpipe
[| eval risk_object=if(isnotnull(field_user),field_user,null()),risk_object_type=if(isnotnull(field_user),"user",null())]
| appendpipe
[| eval risk_object=if(isnotnull(field_ip),field_ip,null()),risk_object_type=if(isnotnull(field_ip),"system",null())]
| eval risk_score=20
| fields - _time field_user field_ip field_host