Join the Conversation
- Find Answers
- :
- Splunk Platform
- :
- Splunk Cloud Platform
- :
- Why does the data gets truncated with csv ingestio...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Why does the data gets truncated with csv ingestion?
Hi,
When I am ingesting a csv file to splunk cloud, few events gets truncated from the file. How to resolve this?
sourcetype=csv
I have used forwarder level props.conf
[csv]
INDEXED_EXTRACTIONS=csv
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
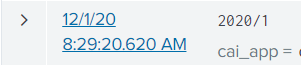
This was one of the event which only has year and rest of the data is not there ,,,other part of data is in separate event . Every time its happing with 7-8 events from a file of 800 events.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
timeStamp,label,responseCode,Hostname
2020/10/29 19:14:12,3 /xxxxxx,302,xxxxxxxx
2020/10/29 19:14:15,Forgot your ID or password?,200,xxxxxxxx
2020/10/29 19:14:19,Signup for free,200,xxxxxxxxxx
2020/10/29 19:14:23,3 /xxxxxxxxxx,302,xxxxxxxxx
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for the sample data.
This is the second time you've ignored my question about where the events are truncated. We need to know more about the problem to understand what may be going wrong.
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Below is the inputs:
[monitor://path]
index = xyz
sourcetype = csv
disabled = false
We also tried to add props at the indexing tier but results were same.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Where are the events truncated? Is it after a certain length, a certain field, a certain character, or something else?
Can you share the first few lines of a sample file? Sanitize as needed, but please don't ruin the context.
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
1. events are getting truncated and not dropped. Events are small
timeStamp,label,responseCode,Hostname
file size is 80 kb
2. Using a Universal forwarder
3.
I have used forwarder level props.conf
[csv]
INDEXED_EXTRACTIONS=csv
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Where are events truncated?
That props.conf should be on the indexer (or heavy forwarder, if the CSV passes through one) rather than the UF.
Please share the inputs.conf settings for the CSV.
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Much more information is needed.
Define "few". Are events getting truncated or are events being dropped? How big are the events? How big is the file?
Which type of forwarder are you using?
Do you have any custom props.conf settings? If so, what are they and where are they placed?
If this reply helps you, Karma would be appreciated.