- Splunk Answers
- :
- Splunk Platform Products
- :
- Splunk Cloud Platform
- :
- Re: Using an IAM role with AWS SQS-Based S3 Input
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Using an IAM role with AWS SQS-Based S3 Input
Hello,
I would like to use an IAM Role with the AWS SQS-Based S3 Input. My particulars:
Splunk Cloud
Version:
7.2.9
Build: 2dc56eaf3546
Splunk Add-on for AWS
Version:
4.6.1
Build:
14
Note, this is on an IDM. Based on other community posts, it appears that I would need to complete the following steps:
-Create the IAM role (R) in my account (AC) with the necessary permissions
-Create a user (U) in AC that can assume R
-Add U's Access Key Identifier, and Access Key as an account (A) under Configurations -> Account.
-Add R as an IAM role (I) under Configurations -> IAM Role
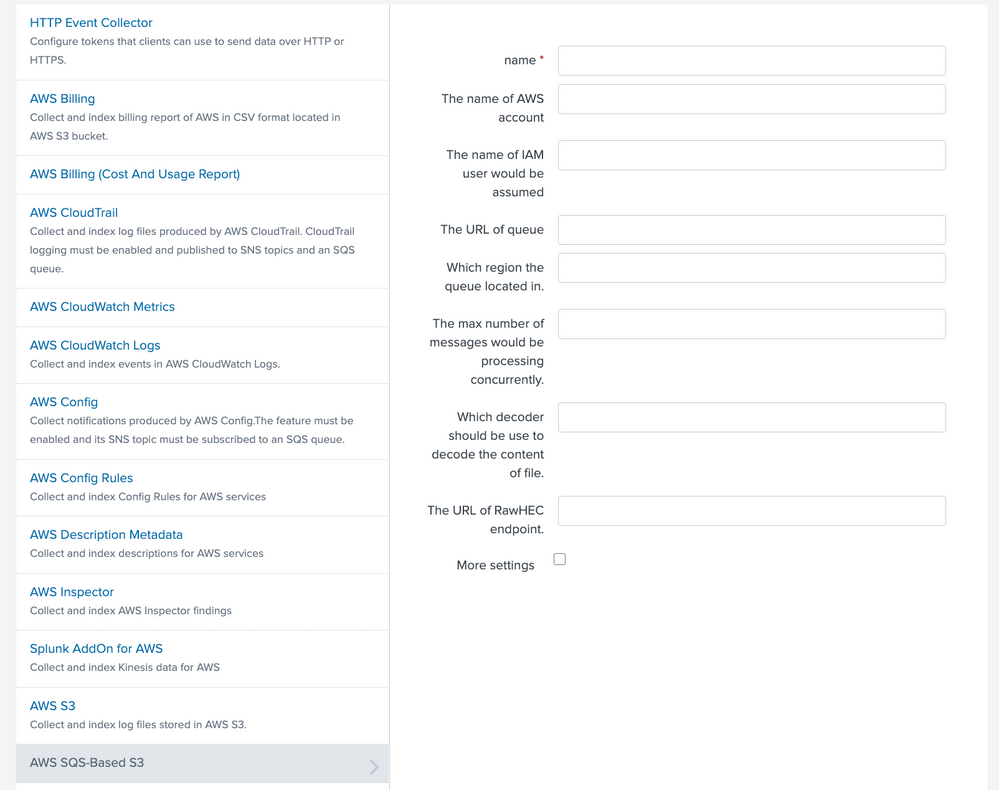
So my question is, on the following screen, would I specify A for 'The name of AWS account' and I as "The name of IAM user would be assumed" (shouldn't this be labeled "The name of IAM Role to assume"?)? Is there a more direct way to accomplish this e.g., the Splunk add-on directly assuming the role?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello rpersaud!
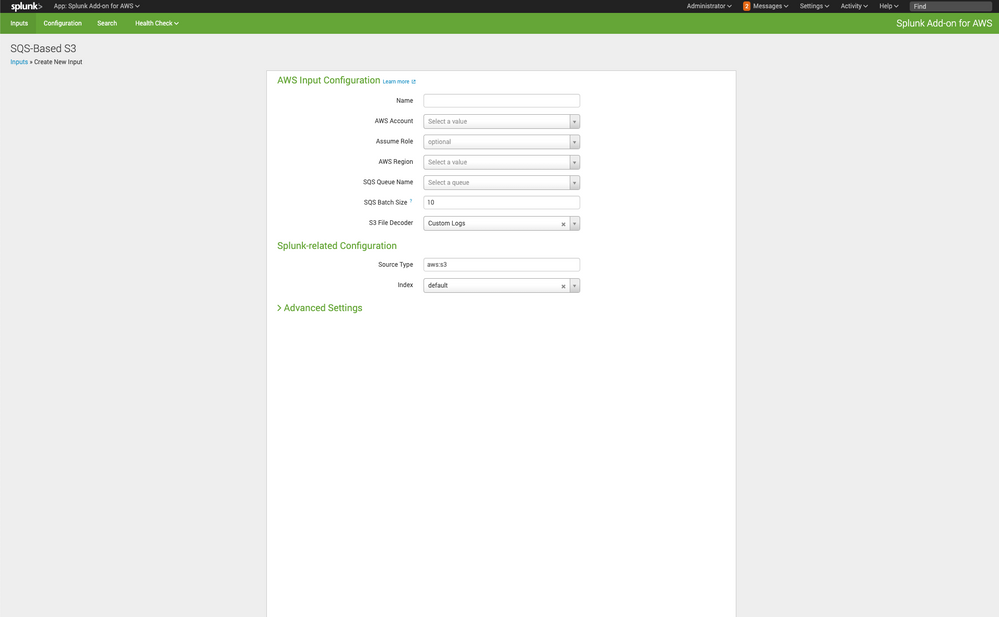
I just fired up my handy AWS/Splunk box to take a look. I'd suggest navigating to the Splunk Add-On for AWS and add the input there. You'll note from the screenshot I attached that the "Assume Role" is optional. I think the UI presents better as well. If there is a ROLE that you would want to assume, you could place it here, but the IAM account that is used will be the same one you setup your Account with in the Splunk Add-On.
-Tom
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@tsmit, thanks for the quick reply. From the Inputs tab, I am able to see the more informative UI that you included in your screenshot.
I'm not sure what you mean by "the same one you setup your Account with in the Splunk Add-On." We have a couple of AWS accounts that are currently being used by AWS SQS-Based S3 Inputs. They were setup from the Configuration -> Account page, and appear in the 'AWS Account' drop down. Presumably, I could setup another account with the appropriate permissions to assume a role, and then specify that account and the role for 'AWS Account' and 'Assume Role', respectively. However, if an IAM user is required to assume a role, then it probably makes sense to just attach the policy directly to the user since we lose the advantages of using an IAM role.