Join the Conversation
- Find Answers
- :
- Splunk Administration
- :
- Admin Other
- :
- Security
- :
- Re: Timechart percent count of http status code
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have a requirement where I want to show the timechart of 5xx errors percentage by total request.
currently I have
index=cgn http_status=5*|timechart count
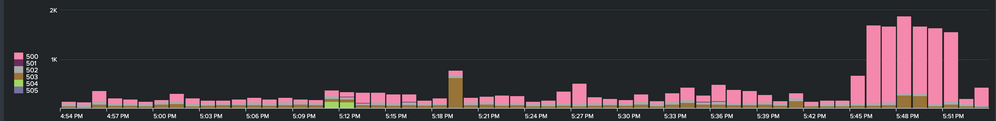
this gives me timechart as
but this does not gives me the real picture as how the backend node doing. so I need to change the chart to percentage of 5xx errors over total request so that I can find out how big the issue is.
Any help?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
There are a number of ways to do this, but it will naturally involve searching all the data to get the totals to then work out the percentage. This will given you a single total percentage for all errors, as well as the individual error counts
index=cgn
| timechart count by status
| addtotals
| addtotals fieldname=Errors 5*
| eval ErrorRate=round(Errors/Total*100,2)
| fields _time 5* ErrorRateand you can then plot the ErrorRate field as a second Y-axis, with its own scale. This gives you best of both worlds in that you can quantify the volume of requests as you have the error counts.
Alternatively if you just want the rate of errors without counts, you can do this
index=cgn
| timechart count by status
| addtotals
| foreach 5* [ addtotals fieldname=tmp_<<MATCHSTR>> 5<<MATCHSTR>> | eval <<FIELD>>=round('tmp_<<MATCHSTR>>'/Total*100,2) ]
| fields _time 5*If you also wanted Total on the right Y-axis, then add Total to the final fields statement and edit the graph accordingly.
Hope this helps
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thankyou! This is beautiful and neat.
Only I have added limit=100 in timechart as I have huge volume of data and 5xx were going as OTHER slice.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
There are a number of ways to do this, but it will naturally involve searching all the data to get the totals to then work out the percentage. This will given you a single total percentage for all errors, as well as the individual error counts
index=cgn
| timechart count by status
| addtotals
| addtotals fieldname=Errors 5*
| eval ErrorRate=round(Errors/Total*100,2)
| fields _time 5* ErrorRateand you can then plot the ErrorRate field as a second Y-axis, with its own scale. This gives you best of both worlds in that you can quantify the volume of requests as you have the error counts.
Alternatively if you just want the rate of errors without counts, you can do this
index=cgn
| timechart count by status
| addtotals
| foreach 5* [ addtotals fieldname=tmp_<<MATCHSTR>> 5<<MATCHSTR>> | eval <<FIELD>>=round('tmp_<<MATCHSTR>>'/Total*100,2) ]
| fields _time 5*If you also wanted Total on the right Y-axis, then add Total to the final fields statement and edit the graph accordingly.
Hope this helps