Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Security
×
Join the Conversation
Without signing in, you're just watching from the sidelines. Sign in or Register to connect, share, and be part of the Splunk Community.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
- Find Answers
- :
- Splunk Administration
- :
- Admin Other
- :
- Security
- :
- Re: Splunk VPC timestamp issue
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Splunk VPC timestamp issue
General_Talos
Path Finder
07-14-2021
04:59 AM
Hey,
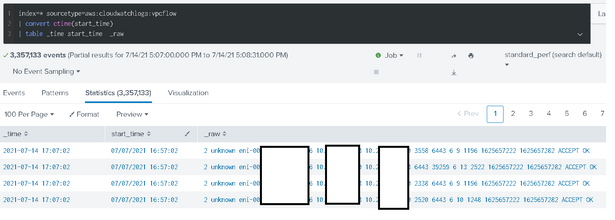
I am sure many of you, who have VPC logs on Splunk have came across this issue.
Raw Log
2 unknown eni-xxxxxxxxxxxxx 192.168.0.10 192.168.0.15 3558 6443 6 9 1196 1625657222 1625657282 ACCEPT OK
Text highlighted in red is event start_time, and I want to replace it with _time
my props.conf
[aws:cloudwatchlogs:vpcflow]
TIME_FORMAT = %s
SHOULD_LINEMERGE = false
TIME_PREFIX = ^(?>\S+\s){10}
MAX_TIMESTAMP_LOOKAHEAD = 10
Still no luck 😞
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
ITWhisperer

SplunkTrust
07-14-2021
05:15 AM
Try this
TIME_PREFIX = (\S+\s+){10}- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
General_Talos
Path Finder
07-14-2021
10:58 AM
Hello @ITWhisperer , thks for sharing. Still the same.
Get Updates on the Splunk Community!
AI for AppInspect
We’re excited to announce two new updates to AppInspect designed to save you time and make the app approval ...
App Platform's 2025 Year in Review: A Year of Innovation, Growth, and Community
As we step into 2026, it’s the perfect moment to reflect on what an extraordinary year 2025 was for the Splunk ...
Operationalizing Entity Risk Score with Enterprise Security 8.3+
Overview
Enterprise Security 8.3 introduces a powerful new feature called “Entity Risk Scoring” (ERS) for ...