- Find Answers
- :
- Splunk Administration
- :
- Admin Other
- :
- Security
- :
- How can I generate a list of users and assigned ro...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I am doing some refactoring of authentication.conf and would like to be able to diff the users and their mapped roles before and after the refactoring. Is there a way to get a list of users and roles?
If it makes a difference I am using a LDAP strategy.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This should get you list of users and their corresponding roles. Need admin privileges to get full result.
|rest /services/authentication/users splunk_server=local
|fields title roles realname|rename title as userName|rename realname as Name
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
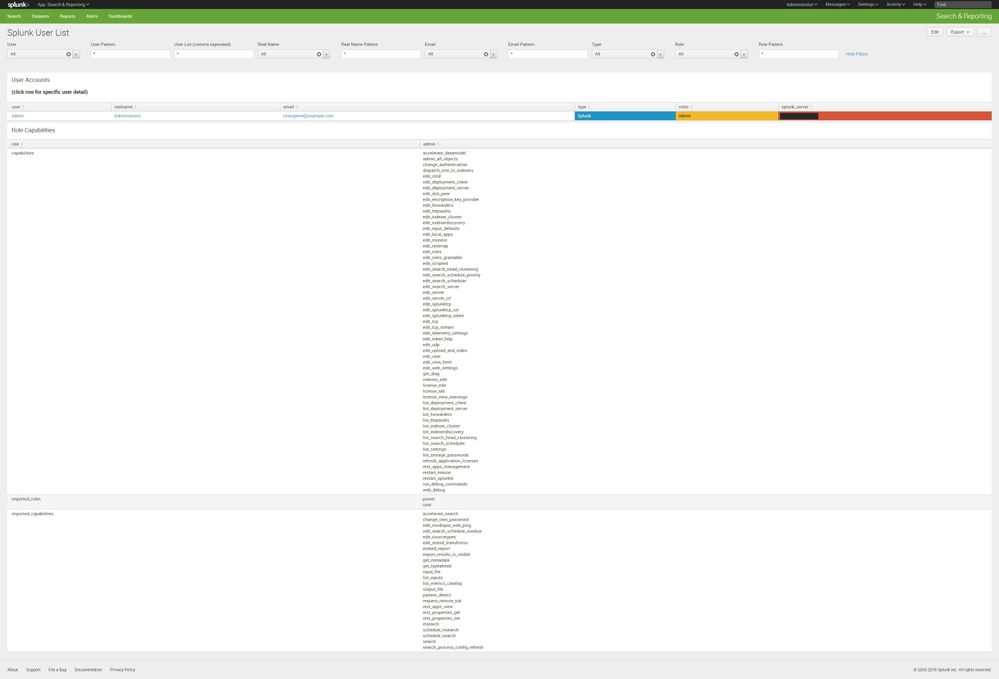
Dashboard of Splunk Users showing roles/capabilities, and index access.
Dashboard Code:
<form>
<label>Splunk User List</label>
<fieldset submitButton="false">
<input type="dropdown" token="user" searchWhenChanged="true">
<label>User</label>
<choice value="*">All</choice>
<default>*</default>
<fieldForLabel>user</fieldForLabel>
<fieldForValue>user</fieldForValue>
<search>
<query>| rest /services/authentication/users splunk_server=local
| table defaultApp id realname email roles type splunk_server capabilities
| replace "*%40*" with "*@*" in id
| rex field=id "/users/(?<user>.+)$"
| table user
| sort user</query>
</search>
</input>
<input type="text" token="user_pattern" searchWhenChanged="true">
<label>User Pattern</label>
<default>*</default>
</input>
<input type="text" token="user_list" searchWhenChanged="true">
<label>User List (comma seperated)</label>
<default>*</default>
</input>
<input type="dropdown" token="real_name" searchWhenChanged="true">
<label>Real Name</label>
<choice value="*">All</choice>
<default>*</default>
<fieldForLabel>realname</fieldForLabel>
<fieldForValue>realname</fieldForValue>
<search>
<query>| rest /services/authentication/users splunk_server=local
| dedup realname
| table realname
| sort realname</query>
<earliest>-24h@h</earliest>
<latest>now</latest>
</search>
</input>
<input type="text" token="real_name_pattern" searchWhenChanged="true">
<label>Real Name Pattern</label>
<default>*</default>
</input>
<input type="dropdown" token="email" searchWhenChanged="true">
<label>Email</label>
<choice value="*">All</choice>
<fieldForLabel>email</fieldForLabel>
<fieldForValue>email</fieldForValue>
<default>*</default>
<search>
<query>| rest /services/authentication/users splunk_server=local
| dedup email
| table email
| sort email</query>
</search>
</input>
<input type="text" token="email_pattern" searchWhenChanged="true">
<label>Email Pattern</label>
<default>*</default>
</input>
<input type="dropdown" token="type" searchWhenChanged="true">
<label>Type</label>
<choice value="*">All</choice>
<default>*</default>
<fieldForLabel>type</fieldForLabel>
<fieldForValue>type</fieldForValue>
<search>
<query>| rest /services/authentication/users splunk_server=local
| dedup type
| table type
| sort type</query>
<earliest>-24h@h</earliest>
<latest>now</latest>
</search>
</input>
<input type="dropdown" token="role" searchWhenChanged="true">
<label>Role</label>
<choice value="*">All</choice>
<fieldForLabel>roles</fieldForLabel>
<fieldForValue>roles</fieldForValue>
<search>
<query>| rest /services/authentication/users splunk_server=local
| table roles
| mvexpand roles
| dedup roles
| table roles
| sort roles</query>
<earliest>-24h@h</earliest>
<latest>now</latest>
</search>
<default>*</default>
</input>
<input type="text" token="role_pattern" searchWhenChanged="true">
<label>Role Pattern</label>
<default>*</default>
</input>
</fieldset>
<row>
<panel>
<title>User Accounts</title>
<table>
<title>(click row for specific user detail)</title>
<search>
<query>| rest /services/authentication/users splunk_server=local
| search realname="$real_name$" realname="*$real_name_pattern$*" email="$email$" email="*$email_pattern$*" roles="$role$" roles="*$role_pattern$*" type="$type$"
| table defaultApp id realname email roles type splunk_server capabilities
| replace "*%40*" with "*@*" in id
| rex field=id "/users/(?<user>.+)$"
| table user realname email type roles splunk_server
| search user="$user$" user="*$user_pattern$*" user IN ($user_list$)
| sort -type user</query>
<earliest>0</earliest>
<latest></latest>
<sampleRatio>1</sampleRatio>
</search>
<option name="count">20</option>
<option name="dataOverlayMode">none</option>
<option name="drilldown">cell</option>
<option name="refresh.display">progressbar</option>
<format type="color" field="action">
<colorPalette type="sharedList"></colorPalette>
<scale type="sharedCategory"></scale>
</format>
<format type="color" field="host">
<colorPalette type="sharedList"></colorPalette>
<scale type="sharedCategory"></scale>
</format>
<format type="color" field="type">
<colorPalette type="sharedList"></colorPalette>
<scale type="sharedCategory"></scale>
</format>
<format type="color" field="roles">
<colorPalette type="sharedList"></colorPalette>
<scale type="sharedCategory"></scale>
</format>
<format type="color" field="splunk_server">
<colorPalette type="sharedList"></colorPalette>
<scale type="sharedCategory"></scale>
</format>
<drilldown>
<unset token="user"></unset>
<set token="user">$click.value$</set>
</drilldown>
</table>
</panel>
</row>
<row>
<panel>
<title>Role Capabilities</title>
<table>
<search>
<query>| rest /services/authentication/users splunk_server=local
| search realname="$real_name$" realname="*$real_name_pattern$*" email="$email$" email="*$email_pattern$*" roles="$role$" roles="*$role_pattern$*" type="$type$"
| table defaultApp id realname email roles type splunk_server
| replace "*%40*" with "*@*" in id
| rex field=id "/users/(?<user>.+)$"
| table user realname email type roles splunk_server
| search user="$user$" user="***" user IN (*)
| rename roles as role
| table role
| mvexpand role
| dedup role
| join role
[| rest /services/authorization/roles
| table title capabilities imported_roles imported_capabilities
| dedup title
| rename title as role
| table role capabilities imported_roles imported_capabilities ]
| table role capabilities imported_roles imported_capabilities
| sort role
| transpose 1000 column_name=role header_field=role</query>
<earliest>0</earliest>
<latest></latest>
<sampleRatio>1</sampleRatio>
</search>
<option name="count">10</option>
<option name="dataOverlayMode">none</option>
<option name="drilldown">none</option>
<option name="refresh.display">progressbar</option>
<format type="color" field="action">
<colorPalette type="sharedList"></colorPalette>
<scale type="sharedCategory"></scale>
</format>
<format type="color" field="host">
<colorPalette type="sharedList"></colorPalette>
<scale type="sharedCategory"></scale>
</format>
<format type="color" field="type">
<colorPalette type="sharedList"></colorPalette>
<scale type="sharedCategory"></scale>
</format>
<format type="color" field="roles">
<colorPalette type="sharedList"></colorPalette>
<scale type="sharedCategory"></scale>
</format>
<format type="color" field="splunk_server">
<colorPalette type="sharedList"></colorPalette>
<scale type="sharedCategory"></scale>
</format>
</table>
</panel>
</row>
<row>
<panel>
<title>Role Index Access</title>
<table>
<search>
<query>| rest /services/authentication/users splunk_server=local
| search realname="$real_name$" realname="*$real_name_pattern$*" email="$email$" email="*$email_pattern$*" roles="$role$" roles="*$role_pattern$*" type="$type$"
| table defaultApp id realname email roles type splunk_server
| replace "*%40*" with "*@*" in id
| rex field=id "/users/(?<user>.+)$"
| table user realname email type roles splunk_server
| search user="$user$" user="***" user IN (*)
| rename roles as role
| table role
| mvexpand role
| dedup role
| join role
[| rest /services/authorization/roles
| table title srchIndexesAllowed imported_roles imported_srchIndexesAllowed
| dedup title
| rename title as role
| table role srchIndexesAllowed imported_roles imported_srchIndexesAllowed ]
| table role srchIndexesAllowed imported_roles imported_srchIndexesAllowed
| sort role
| transpose 1000 column_name=role header_field=role</query>
<earliest>0</earliest>
<latest></latest>
<sampleRatio>1</sampleRatio>
</search>
<option name="count">10</option>
<option name="dataOverlayMode">none</option>
<option name="drilldown">none</option>
<option name="refresh.display">progressbar</option>
<format type="color" field="action">
<colorPalette type="sharedList"></colorPalette>
<scale type="sharedCategory"></scale>
</format>
<format type="color" field="host">
<colorPalette type="sharedList"></colorPalette>
<scale type="sharedCategory"></scale>
</format>
<format type="color" field="type">
<colorPalette type="sharedList"></colorPalette>
<scale type="sharedCategory"></scale>
</format>
<format type="color" field="roles">
<colorPalette type="sharedList"></colorPalette>
<scale type="sharedCategory"></scale>
</format>
<format type="color" field="splunk_server">
<colorPalette type="sharedList"></colorPalette>
<scale type="sharedCategory"></scale>
</format>
</table>
</panel>
</row>
</form>
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Here is an updated version. Less use of not need table command, use of base search. Dropdown with counters++
<form version="1.1" theme="dark">
<label>List of Users Capabilities</label>
<!--
1.1 based on https://community.splunk.com/t5/Security/How-can-I-generate-a-list-of-users-and-assigned-roles/m-p/194811
-->
<search id="base_search">
<query>
| rest /services/authentication/users splunk_server=local
| replace "*%40*" with "*@*" in id
| rex field=id "/users/(?<user>.+)$"
| rename roles as role
| fields user defaultApp id realname email role type splunk_server capabilities
| search
user="$user$"
type="$type$"
role="$role$"
</query>
</search>
<fieldset submitButton="false" autoRun="false">
<input type="dropdown" token="user">
<label>User</label>
<search base="base_search">
<query>
| eval data=user
| stats count by data realname
| eval info=data." (".realname.")"
| sort data
</query>
</search>
<choice value="*">Any</choice>
<fieldForLabel>info</fieldForLabel>
<fieldForValue>data</fieldForValue>
<default>*</default>
</input>
<input type="dropdown" token="type">
<label>Type</label>
<search base="base_search">
<query>
| eval data=type
| stats count by data
| eval info=data." (".count.")"
| sort -count
</query>
</search>
<choice value="*">Any</choice>
<fieldForLabel>info</fieldForLabel>
<fieldForValue>data</fieldForValue>
<default>*</default>
</input>
<input type="dropdown" token="role">
<label>Role</label>
<search base="base_search">
<query>
| eval data=role
| stats count by data
| eval info=data." (".count.")"
| sort -count
</query>
</search>
<choice value="*">Any</choice>
<fieldForLabel>info</fieldForLabel>
<fieldForValue>data</fieldForValue>
<default>*</default>
</input>
</fieldset>
<row>
<panel>
<title>User Accounts</title>
<table>
<search base="base_search">
<query>
| table user realname email type role splunk_server
</query>
</search>
<option name="count">20</option>
<option name="dataOverlayMode">none</option>
<option name="drilldown">cell</option>
<option name="refresh.display">progressbar</option>
<format type="color" field="action">
<colorPalette type="sharedList"></colorPalette>
<scale type="sharedCategory"></scale>
</format>
<format type="color" field="host">
<colorPalette type="sharedList"></colorPalette>
<scale type="sharedCategory"></scale>
</format>
<format type="color" field="type">
<colorPalette type="sharedList"></colorPalette>
<scale type="sharedCategory"></scale>
</format>
<format type="color" field="role">
<colorPalette type="sharedList"></colorPalette>
<scale type="sharedCategory"></scale>
</format>
<format type="color" field="splunk_server">
<colorPalette type="sharedList"></colorPalette>
<scale type="sharedCategory"></scale>
</format>
<drilldown>
<unset token="user"></unset>
<set token="user">$click.value$</set>
</drilldown>
</table>
</panel>
</row>
<row>
<panel>
<title>Role Capabilities</title>
<table>
<search base="base_search">
<query>
| dedup role
| mvexpand role
| join role
[
| rest /services/authorization/roles
| dedup title
| rename title as role
]
| table role capabilities imported_capabilities
| sort role
| transpose 1000 column_name=role header_field=role
</query>
</search>
<option name="count">10</option>
<option name="dataOverlayMode">none</option>
<option name="drilldown">none</option>
<option name="refresh.display">progressbar</option>
<format type="color" field="action">
<colorPalette type="sharedList"></colorPalette>
<scale type="sharedCategory"></scale>
</format>
<format type="color" field="host">
<colorPalette type="sharedList"></colorPalette>
<scale type="sharedCategory"></scale>
</format>
<format type="color" field="type">
<colorPalette type="sharedList"></colorPalette>
<scale type="sharedCategory"></scale>
</format>
<format type="color" field="roles">
<colorPalette type="sharedList"></colorPalette>
<scale type="sharedCategory"></scale>
</format>
<format type="color" field="splunk_server">
<colorPalette type="sharedList"></colorPalette>
<scale type="sharedCategory"></scale>
</format>
</table>
</panel>
</row>
<row>
<panel>
<title>Role Index Access</title>
<table>
<search base="base_search">
<query>
| table role
| mvexpand role
| dedup role
| join role
[
| rest /services/authorization/roles
| dedup title
| rename title as role
]
| table role srchIndexesAllowed imported_roles imported_srchIndexesAllowed
| sort role
| transpose 1000 column_name=role header_field=role
</query>
</search>
<option name="count">10</option>
<option name="dataOverlayMode">none</option>
<option name="drilldown">none</option>
<option name="refresh.display">progressbar</option>
<format type="color" field="action">
<colorPalette type="sharedList"></colorPalette>
<scale type="sharedCategory"></scale>
</format>
<format type="color" field="host">
<colorPalette type="sharedList"></colorPalette>
<scale type="sharedCategory"></scale>
</format>
<format type="color" field="type">
<colorPalette type="sharedList"></colorPalette>
<scale type="sharedCategory"></scale>
</format>
<format type="color" field="roles">
<colorPalette type="sharedList"></colorPalette>
<scale type="sharedCategory"></scale>
</format>
<format type="color" field="splunk_server">
<colorPalette type="sharedList"></colorPalette>
<scale type="sharedCategory"></scale>
</format>
</table>
</panel>
</row>
</form>
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Holy Cow, great stuff -- thanks!
why, oh why, could Splunk not have had something like this...?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Great stuff!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Most excellent, ty
Search to indicate what roles can search the index:
| rest /services/authorization/roles splunk_server=local | table id, srchIndexesAllowed | mvexpand srchIndexesAllowed | search srchIndexesAllowed="IndexName"
Search to indicate what roles can search all indexes
| rest /services/authorization/roles splunk_server=local | table id, srchIndexesAllowed | mvexpand srchIndexesAllowed | where match(srchIndexesAllowed,"[*]")
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This should get you list of users and their corresponding roles. Need admin privileges to get full result.
|rest /services/authentication/users splunk_server=local
|fields title roles realname|rename title as userName|rename realname as Name
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This rest api call, as mentioned, must have the admin privilege otherwise you won't get the result. I granted a regular user ALL the capabilities it still won't work. Only a user with admin privilege can run it. To use it in a search for a dashboard for non-admin will not work. You need to create a savedsearch as admin and use the savedsearch in the dashboard.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@somesoni2,
I cant thank you enough for how many times I have taken your answers 🙂
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
|rest /services/authentication/users | search realname=* roles!=app* roles!=index* | dedup title type realname email tz roles
| table title type realname email tz roles | rename title as Username realname as "Full name" tz AS "Time zone" email AS "Email address" type AS "Authentication system"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nice query somesoni2,
and nice enhancement landen99.
Thank you very much. That's very helpful.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It could be because of roles field is multivalue field. Try by adding "| nomv roles" at the end of the search.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This search does not seem to play nice with the export results option...the output csv comes out empty. Any idea why? How to work around it?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks a bunch!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How would you change the splunk_server=local to get all user roles across the network?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
splunk_server=*
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'm open to using whatever tool makes the most sense...a splunk search would be awesome, or if btool can do it that is fine too. I just want to create a list before and after to diff.