- Find Answers
- :
- Splunk Administration
- :
- Admin Other
- :
- Security
- :
- Field Extraction with transforms configuration
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
I have issues getting expected field value pairs using following props and transforms configuration files. Sample events and my configuration files are given below. Any recommendation will be highly appreciated.
My Configuration Files
[mypropsfile]
REPORT-mytranforms=myTransfile
[myTransfile]
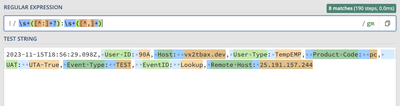
REGEX = ([^"]+?):\s+([^"]+?)
FORMAT = $1::$2
Sample Events
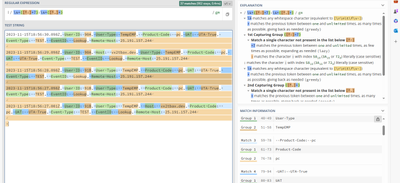
2023-11-15T18:56:30.098Z, User ID: 90A, User Type: TempEMP, Product Code: pc, UAT: UTA-True, Event Type: TEST, EventID: Lookup, Remote Host: 25.191.157.244
2023-11-15T18:56:29.098Z, User ID: 90A, Host: vx2tbax.dev, User Type: TempEMP, Product Code: pc, UAT: UTA-True, Event Type: TEST, EventID: Lookup, Remote Host: 25.191.157.244
2023-11-15T18:56:28.098Z, User ID: 91B, User Type: TempEMP, Product Code: pc, UAT: UTA-True, Event Type: TEST, EventID: Lookup, Remote Host: 25.191.157.244
2023-11-15T18:56:27.098Z, User ID: 91B, User Type: TempEMP, Product Code: pc, UAT: UTA-True, Event Type: TEST, EventID: Lookup, Remote Host: 25.191.157.244
2023-11-15T18:56:27.001Z, User ID: 91B, User Type: TempEMP, Host: vx2tbax.dev, Product Code: pc, UAT: UTA-True, Event Type: TEST, EventID: Lookup, Remote Host: 25.191.157.244
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
First glance it looks like this the regex you provided is looking for double quote to help find the pattern and the sample event don't seem to have any.
I think you may have better luck using a regex closer to
REGEX = \s+([^:]+?):\s+([^,]+)
I havent tested locally but on regex 101 it looks like it matches pretty well
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
First glance it looks like this the regex you provided is looking for double quote to help find the pattern and the sample event don't seem to have any.
I think you may have better luck using a regex closer to
REGEX = \s+([^:]+?):\s+([^,]+)
I havent tested locally but on regex 101 it looks like it matches pretty well
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello @dtburrows3,
Thank you so much for your quick response, truly appreciate it. I am getting this: