Join the Conversation
- Find Answers
- :
- Using Splunk
- :
- Other Using Splunk
- :
- Reporting
- :
- How do I set a trigger condition on a Splunk repor...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
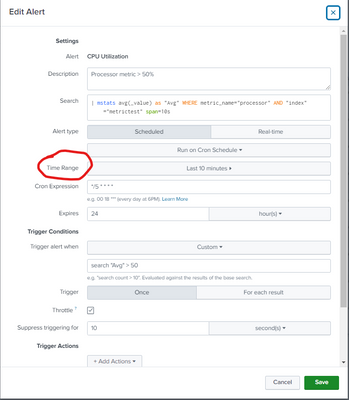
How do I set a trigger condition on a Splunk report like you would when creating an alert?
How do I set a "Trigger Condition" on a Splunk report like you would when creating an alert?
My issue is that I have created a report that I want to generate an email from when Number of Results = 0 ie, when no file has been uploaded/detected.
Some people would argue why don't I just create an alert instead? My dilemma is, with an alert it won’t let you add a "Time Range" as I want my daily report to track the previous 7 day time range
My search string looks like this:
index=it_sts_xfer_prod_us xferPath="*GIDM*" OR xferPath="*sailpnt*" OR xferPath="*identity*" OR xferPath="*InternalAudit*" xferFile="FILENAME.csv" | eval _time=_time-xferSecs | convert ctime(_time) as Time timeformat=%m/%d/%y
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Reports don't have triggers. They always send their results.
Alerts have triggers. They also have time ranges.
If this reply helps you, Karma would be appreciated.