Are you a member of the Splunk Community?
- News & Events
- :
- Blog & Announcements
- :
- Product News & Announcements
- :
- Security Highlights: September 2022 Newsletter
Security Highlights: September 2022 Newsletter
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark Topic
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
September 2022
The Splunk App for Fraud Analytics (SFA) is now Splunk Supported
Use your existing Splunk Enterprise Security to gain anti-fraud insights across all of your data sources and remove silos in your fraud prevention strategy. It is well known that fraud is increasing in complexity and has an expanded reach in today’s environment. With SFA, you can better reduce the financial and reputational damage due to fraudulent activity and enhance your anti-fraud programs.
What is The Splunk App for Fraud Analytics?
The Splunk App for Fraud Analytics (SFA) is a comprehensive anti-fraud solution that uses the detection and investigation power of Splunk Enterprise Security (ES). SFA leverages the Risk Based Framework to improve alert fidelity and offers fraud teams a standardized workflow and extensive incident investigation capabilities to improve their anti-fraud strategy.
Detections and Analytic Stories to Stay Ahead of Threats
The Splunk Threat Research Team recently released Enterprise Security Content Update v3.48.0 with 28 new detections and 5 updated analytic stories.
Release highlights include:
- An updated correlation rule based on the risk data model for discovering execution of several Linux binaries used for Living off the Land based attacks typically used for privilege escalation
- New analytics to help secure Azure environments from Active Directory account takeover attacks
The Splunk Threat Research Team also performed a deep dive analysis on Azurolt Loader, a payload that imports its own AppLocker policy to prevent various antivirus software components from executing, and published a blog highlighting the various analytics that can be used to detect this behavior.
The State of Security 2022: Where do we go from here?
Members of the Splunk SURGe team reported on key findings from The State of Security 2022 report and provided strategies to keep up with adversaries and recommendations to strengthen your security. Watch the webinar here.
A Beginners Guide to SOAR - How to Automate 5 Security Processes in Under 30 Minutes
Wondering how to get started on your journey with security orchestration and automation? Watch the webinar to learn how to build the following five automation playbooks with Splunk SOAR:
- Investigate a URL
- Investigate a domain
- Enrich phishing alerts
- Create a ticket, quarantine a host, and block a domain
- Perform and end-to-end investigation from a risk notable received from Splunk Enterprise Security
SIEM and SOAR - An Automation Powerhouse for Cyber Incident Response
With attacks becoming more sophisticated, time is a key factor when managing incidents in a large enterprise where different security controls generate thousands of alerts. Watch this webinar to see how the combination of Splunk SOAR and Splunk Enterprise Security creates a framework to streamline security incident response and can reduce threat detection time by 87% and response time by 94%.
RSAC 2022 Top Rated Session - Bingo! 10 Security Standards in 2022 You Can’t Live Without
Kirsty Paine, Splunk Strategic Advisor - Technology and Innovation, and Broadcom CTO, Bret Jordan, had their RSAC presentation covering interesting and impactful technical standards selected by peers as a top-rated session. If you missed it, you can watch the recording and download the slides here.
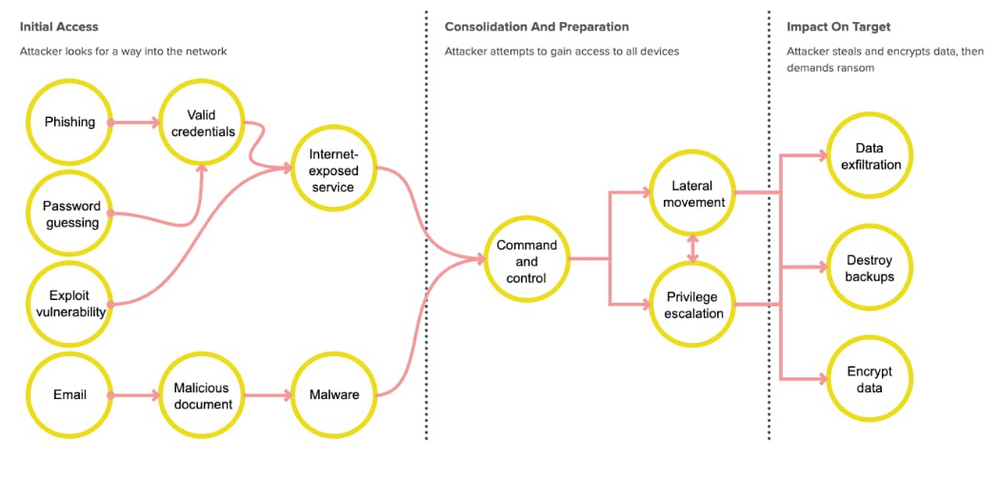
Introducing the Ransomware Content Browser
As part of the recent Splunk Security Essentials (SSE) release, Splunk has developed an interactive online environment where users can interact with the stages and phases of the ransomware attack lifecycle and highlight existing security content to see practical things that can be done as a defender.
Learn more about the Ransomware Content Browser in this blog.
Do More with Lantern
Splunk Lantern published 11 new articles in August, including an updated FAQ for the Splunk Platform 9.0.1 release. In addition to this great content, we've made the following updates.
- We rebranded from a "Resource Center" to a "Customer Success Center". We want to make clear that we are here to help you succeed with Splunk. If you need help getting started with a new product, learning how to ingest a new data source, or figuring out how to implement an observability use case, we're here for you. All our articles are written by Splunk experts who work in the field every day with customers just like you, so you know you're getting the best guidance possible to get you Splunking your data faster and better
- We’ve launched a new feedback widget on our site! The orange tab on the left-hand side allows you to tell us how articles are working for you or where improvement is needed. The survey is anonymous, so you won’t be able to receive a direct response to any comments you leave. However, you can always talk to us directly on the Splunk User Groups Slack or Reddit. Please take the time to leave feedback on our articles so we can make sure our content is effective in helping you succeed with Splunk!
- Finally, if you have been accessing Splunk Lantern articles using the knowledge bots of the Splunk Product Guidance app in Splunk Cloud Platform, please note that those bots have been removed based on feedback. We apologize if you found those bots helpful, but don't worry - none of the great content has gone away. You can still search for help with SPL and data source onboarding at any time on lantern.splunk.com

New Splunkbase Preview
Have you tried the new Splunkbase preview? Soon it will exit preview and become the default view for Splunkbase! But why wait? Visit today and experience the faster page loads, better search results, cleaner app directory and app cards and more!
An App for Clearer Queries and Better Results?
Security and IT analysts need to be able to find threats and issues without having to write complex search queries. The Splunk Common Information Model (CIM) app delivers a common lexicon of field names and event types across different vendor data sources making them consistent so that analysts can write clearer queries and get better results with more true positives and fewer false positives.
Learn more in this “Introduction to Splunk Common Information Model” video and in the .conf22 “Finding Threats Better With Splunk® Common Information Model (CIM) in Your Searches and Custom Add-o...” session.
New and Recent Updates
Are you using Puppet for IT automation? The recently updated Puppet Report Viewer app for Splunk integrates Puppet Enterprise or Puppet open source with Splunk to send Puppet node inventory, node facts, report summaries and report details into Splunk from one or more Puppet primary servers and automate taking action by triggering Bolt tasks from Actionable Alerts. See the app
The Splunk Add-on for Google Workspace allows a Splunk administrator to collect Google Workspace event data using Google Workspace APIs. You can then analyze the data in the Splunk platform.
The Splunk App for Zoom provides the interface for searches, reports, and dashboards for your Zoom video conferencing environment. It works in concert with Splunk Connect for Zoom, which connects to your Zoom data, to enable you to monitor, manage, and troubleshoot your Zoom service from a single application.
Have you ever wanted to perform advanced text analytics inside Splunk? Splunk has some ways to handle text but also lacks some more advanced features that NLP libraries can offer. The NLP Text Analytics app provides a simple interface for analyzing text in Splunk using python natural language processing libraries. This can also benefit use-cases that involve using Splunk’s ML Toolkit.

Ongoing Blog Series on OpenTelemetry: Everything you Wanted to Know About Sending Logs to Splunk (With the new OpenTelemetry Collector)
Curious about OpenTelemetry but more interested in logs than APM tracing or metrics? Look no further! This blog post will walk you through your first OpenTelemetry Logging pipeline. The OpenTelemetry project is the second largest project of the Cloud Native Computing Foundation (CNCF).
Read more to learn about sending logs to Splunk with the new OpenTelemetry Collector!
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.