Join the Conversation
- Find Answers
- :
- Splunk Administration
- :
- Admin Other
- :
- Installation
- :
- How do you interpret string variable as SPL in Map...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Background
I have a variety of firewall logs that I use to monitor if specific applications are up and running. If there are no firewall logs about that application, it alerts me if the application is down. I did not want to create an individual alert for each application because that gets difficult to manage. Instead, I want to create one alert that iterates over a lookup .CSV file and tests all cases configured in it.
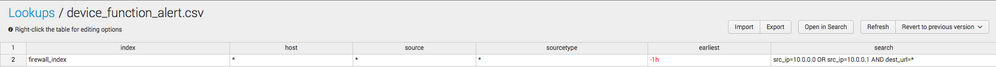
The structure of this lookup file is:
The Alert SPL is:
| inputlookup device_function_alert.csv
`comment("Run the below search for each row in the lookup")`
| map maxsearches=1000 search="search index=$index$ host=$host$ source=$source$ sourcetype=$sourcetype$ earliest=$earliest$ $search$
| fields index, host, source, sourcetype, _time
`comment("Append pipe creates a result for events where the search returned nothing")`
| appendpipe [ stats count]
| eval index=\"$index$\"
| eval host=\"$host$\"
| eval source=\"$source$\"
| eval sourcetype=\"$sourcetype$\"
| stats earliest(_time) AS oldest_log count by index, host, source, sourcetype
`comment("If there is no earliest time on the logs then no events were found and set count to 0")`
| eval count=if(isnull(oldest_log), 0, count)"
| where count==0
Problem
This search works perfectly except for the $search$ variable. The search parser interprets the first line of the map search as
index=firewall_index host="*" source="*" sourcetype="*" earliest="-1h" "src_ip=10.0.0.0 OR src_ip=10.0.0.1 AND dest_url=*"
The $search$ variable was treated as a string and not as SPL. So it searched for literal match of
"src_ip=10.0.0.0 OR src_ip=10.0.0.1 AND dest_url=*"
Is there a way in Splunk to have the search parser see a field as SPL and interpret it as such inside a Map function?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You can cheat:
| makeresults | eval search = "index=_internal sourcetype=splunkd*" | map [search [makeresults | eval search=$search$ | table search] | stats count by sourcetype]
The subsearch will effectively unwrap the string from its double quotes. Not pretty, but it works...
Same thing can be achieved with a macro:
| makeresults | eval search = "index=_internal sourcetype=splunkd*" | map search="search `unwrap($search$)` | stats count by sourcetype"
The macro is defined like this:
[unwrap(1)]
args = arg
definition = $arg$
iseval = 0
In general, things involving map often turn towards the hacky side of life.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You can cheat:
| makeresults | eval search = "index=_internal sourcetype=splunkd*" | map [search [makeresults | eval search=$search$ | table search] | stats count by sourcetype]
The subsearch will effectively unwrap the string from its double quotes. Not pretty, but it works...
Same thing can be achieved with a macro:
| makeresults | eval search = "index=_internal sourcetype=splunkd*" | map search="search `unwrap($search$)` | stats count by sourcetype"
The macro is defined like this:
[unwrap(1)]
args = arg
definition = $arg$
iseval = 0
In general, things involving map often turn towards the hacky side of life.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you! This worked very well! I had been hitting a wall with this problem.