- Find Answers
- :
- Splunk Administration
- :
- Getting Data In
- :
- duplicate host field when _raw is json
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
duplicate host field when _raw is json
Hi all,
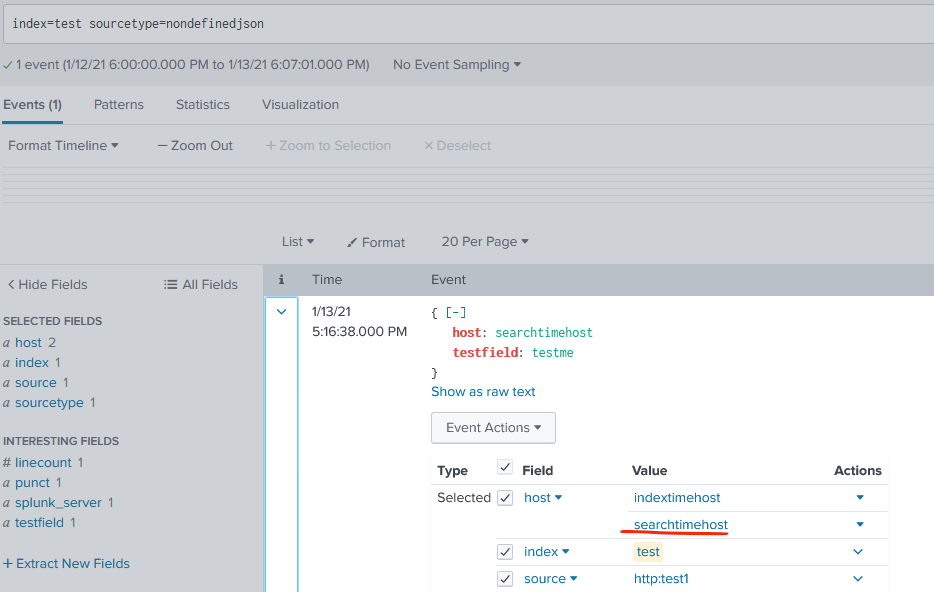
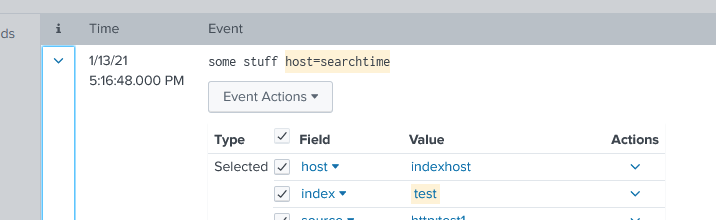
I'm having non-indexed-extracted json in events. When there is a json "host" field host, which is different from the indexed "host", then the search view is showing you 2 values for host in smart or verbose mode.
you can't work with the searchtime extracted json host field - clicking on it gives you no results - as host is an indexed field.
.. when you are doing a ... | stats count by host, then only "indextimehost" is reported back - as expected.
this behaviour differers from "normal" kv searchtime detection:
i found multiple posts regarding this like:
unfortunately i'm not able to change the json field name at the source. Rewriting is also no good option for me.
This more looks like a display bug for me.. but drives the poweruser crasy.
best Regards,
Andreas
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
index=_internal | head 1 | fields _raw host
| eval _raw="{\"host\": \"your host\"}"
| spath
In default, KV_MODE=auto. so json is extracted, so if the event has the same name, it will inevitably become.
index=_internal | head 1 | fields _raw host
| eval _raw="{\"host\": \"your host\"}"
| eval hostname=spath(_raw,"host")
how about this?