Are you a member of the Splunk Community?
- Find Answers
- :
- Splunk Administration
- :
- Getting Data In
- :
- Would like to reformat event at ingestion time to ...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Would like to reformat event at ingestion time to avoid rex/rename in queries
Currently the app I'm working on generates log events in the following (simplified/obfuscated) format before they are ingested into Splunk:
2021-09-24 19:00:00.016 +00:00 [Warning] Something.SomethingElse.YetAnotherThing: jsonData={ "alice": "Alison", "bob": "Bobby", "group" : {"joe": "Joseph", "jane": "Janet"}}
The only bits of those log events which are important are the timestamp at the leftmost end, and the well-formed json data after the equal sign.
What I wish was possible is to change the event being created by the application to be only a well-formed JSON object that included the timestamp. In other words something like this....
{"_time":"2021-09-24 19:00:00.016 +00:00", "alice": "Alison", "bob": "Bobby", "thing" : {"joe": "Joseph", "jane": "Janet"}}
But that is it's own challenge (outside of Splunk) which will take me time to make happen. In the meantime I wonder if there is something I could setup in Splunk so that, at ingestion time, the original log event was transformed into that latter format. This would save me from having to do rex & rename commands like this as part of each an every splunk query I want to run. Which is not only annoying, but I'm guessing slows down the queries as well.
host="something"
| rex "jsonData=(?<jsonData>.+})"
| rename jsonData as _raw
| spath
| search event="*Exception*"
Is this possible? Furthermore is this possible given that the events are ingested from Azure via the plugin: Splunk Add-on for Microsoft Cloud Services?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Try using SEDCMD. Put this in your props.conf file (in the appropriate stanza):
SEDCMD-keepJSON = s/\[.*jsonData/jsonData/If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It seems I left out a relevant fact, we are using Splunk Cloud and therefore don't have access to that file.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
That is key information to not leave out, but you still can update props.conf. Put the file in an app and install the app.
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
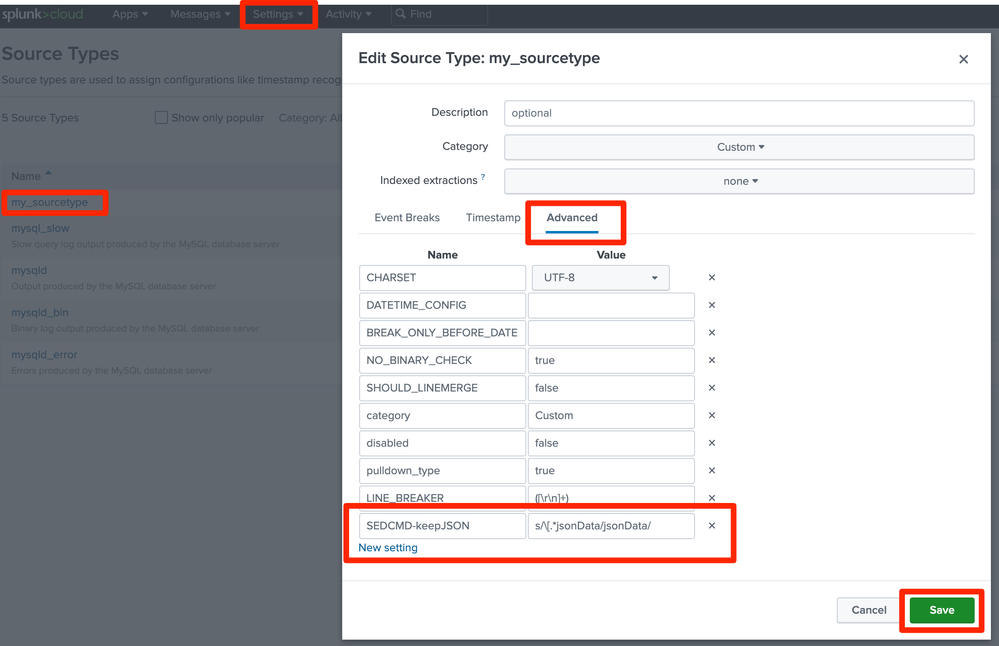
It's possible to do this type of thing in the UI too. Go to Settings > Source Types > choose the sourcetype > Advanced > New setting > Save
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Due to my lack of familiarity with the props.conf file this is a very attractive solution. Thanks!