Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Getting Data In
×
Are you a member of the Splunk Community?
Sign in or Register with your Splunk account to get your questions answered, access valuable resources and connect with experts!
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
- Find Answers
- :
- Splunk Administration
- :
- Getting Data In
- :
- Why does INGEST_EVAL duplicate my events if I assi...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
peter_krammer
Communicator
08-05-2021
06:58 AM
When I configure INGEST_EVAL to replace _raw with something else, it duplicates the event.
Splunk Enterprise Version 8.2.1
props.conf:
Spoiler
[source::http:splunk_hec_token]
TRUNCATE = 500000
SHOULD_LINEMERGE = false
KV_MODE = json
TRANSFORMS-fdz_event = fdz_event
TRUNCATE = 500000
SHOULD_LINEMERGE = false
KV_MODE = json
TRANSFORMS-fdz_event = fdz_event
transforms.conf
Spoiler
[fdz_event]
INGEST_EVAL = _raw="Test"
INGEST_EVAL = _raw="Test"
Output:
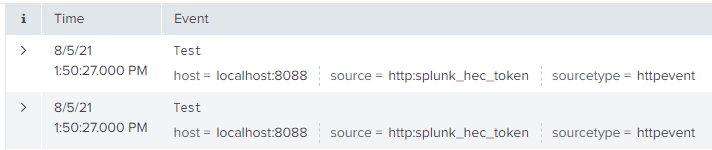
1 Solution
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
peter_krammer
Communicator
08-05-2021
07:50 AM
I found a workaround to circumvent this bug.
tranforms.conf
Spoiler
[fdz_event]
INGEST_EVAL = _raw="Test", queue=if(isnull(timestamp),"nullQueue", queue)
INGEST_EVAL = _raw="Test", queue=if(isnull(timestamp),"nullQueue", queue)
Because I notices that one of the duplicates has an indexed field "timestamp::none" and the other does not. With this I am routing only one of the to the nullQueue and keep the other.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
peter_krammer
Communicator
08-05-2021
07:50 AM
I found a workaround to circumvent this bug.
tranforms.conf
Spoiler
[fdz_event]
INGEST_EVAL = _raw="Test", queue=if(isnull(timestamp),"nullQueue", queue)
INGEST_EVAL = _raw="Test", queue=if(isnull(timestamp),"nullQueue", queue)
Because I notices that one of the duplicates has an indexed field "timestamp::none" and the other does not. With this I am routing only one of the to the nullQueue and keep the other.
Get Updates on the Splunk Community!
What the End of Support for Splunk Add-on Builder Means for You
Hello Splunk Community!
We want to share an important update regarding the future of the Splunk Add-on Builder ...
Solve, Learn, Repeat: New Puzzle Channel Now Live
Welcome to the Splunk Puzzle PlaygroundIf you are anything like me, you love to solve problems, and what ...
Building Reliable Asset and Identity Frameworks in Splunk ES
Accurate asset and identity resolution is the backbone of security operations. Without it, alerts are ...
