Join the Conversation
- Find Answers
- :
- Splunk Administration
- :
- Getting Data In
- :
- Re: UF data going to wrong index
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
UF data going to wrong index
I have a UF on an rsyslog server. The UF is forwarding logs to the indexer successfully, but one of my two input flows is going to the wrong index, and I can't figure it out.
inputs.conf
[monitor:///path/number/one/*]
index = first_index
sourcetype = first_index
host_segment = 4
disabled = false
[monitor:///path/number/two/*]
index = second_index
sourcetype = second_index
host_segment = 4
disabled = falseData of sourcetype second_index makes it to the corresponding index, but data of sourcetype first_index ends up in the main index.
The only props and transforms I have configured are from the VMware add-on and its accessories, but I've scoured its conf files and have not found anything that would send this non-VMware data to main instead of where it belongs when it's specified in $SPLUNK_HOME/etc/system/local/inputs.conf.
Any ideas? Thx!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello @whar_garbl
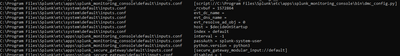
Can you run following btool command from splunk bin directiry to check runtime confguration of inputs config
its shows inputs config from all splunk directory to check any thoer stanza which is taking precence to send the data to main index instaed of first_index for source /path/number/one/*
splunk btool inputs list --debug
sample output