Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Getting Data In
×
Are you a member of the Splunk Community?
Sign in or Register with your Splunk account to get your questions answered, access valuable resources and connect with experts!
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
- Find Answers
- :
- Splunk Administration
- :
- Getting Data In
- :
- Re: Timestamp extraction for varying subseconds an...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Timestamp extraction for varying subseconds and time zones?
ankithreddy777
Contributor
09-07-2018
09:55 AM
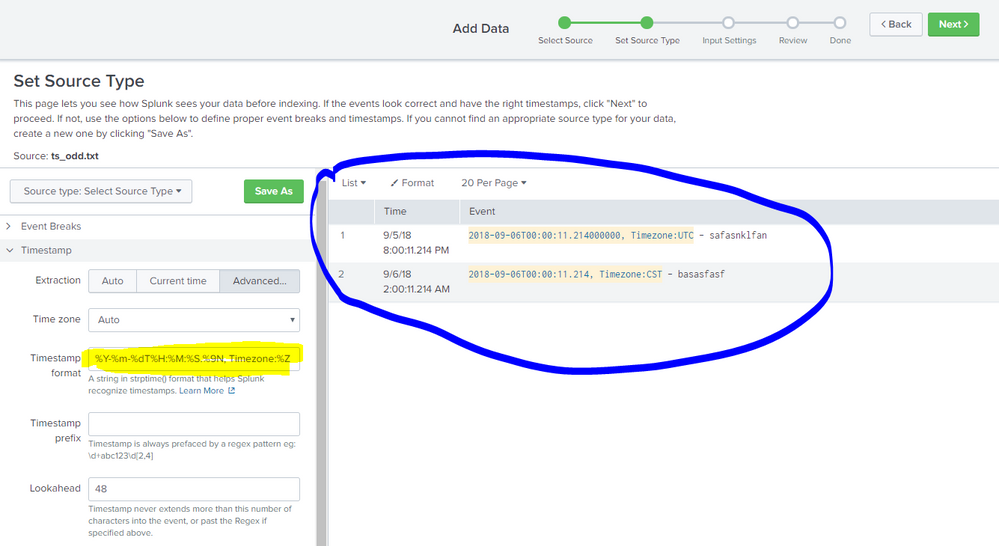
How do you extract a timestamp from message having
event1: Timestamp:2018-09-06T00:00:11.214000000, Timezone:UTC
event2: Timestamp:2018-09-06T00:00:11.214, Timezone:CST
where sub seconds can be milliseconds or nano seconds which vary and time zone can be any string like UTC,CST etc.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
adonio
Ultra Champion
09-07-2018
10:57 AM
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
sudosplunk
Motivator
09-07-2018
10:05 AM
If you have multiple timestamp formats in single log file, then try configuring datetime.xml. Refer to below docs for more information.
http://docs.splunk.com/Documentation/SplunkCloud/latest/Data/Configuredatetimexml
https://www.splunk.com/blog/2014/04/23/its-that-time-again.html
Get Updates on the Splunk Community!
Automatic Discovery Part 1: What is Automatic Discovery in Splunk Observability Cloud ...
If you’ve ever deployed a new database cluster, spun up a caching layer, or added a load balancer, you know it ...
Real-Time Fraud Detection: How Splunk Dashboards Protect Financial Institutions
Financial fraud isn't slowing down. If anything, it's getting more sophisticated. Account takeovers, credit ...
Splunk + ThousandEyes: Correlate frontend, app, and network data to troubleshoot ...
Are you tired of troubleshooting delays caused by siloed frontend, application, and network data? We've got a ...