- Splunk Answers
- :
- Splunk Administration
- :
- Getting Data In
- :
- Splunk Blacklist DesktopExtension.exe addition inp...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello all,
I am trying to blacklist this app that is generating a ton of Windows Event logs; till I find what app it is and uninstall it. This is for HP's DesktopExtension.exe. The weird thing is that it is only running on about 30 devices.
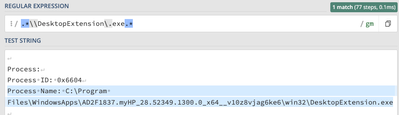
Here is the current section in inputs.conf :
[WinEventLog://Security]
disabled = 0
evt_resolve_ad_obj = 1
checkpointInterval = 5
blacklist1 = EventCode="4662" Message="Object Type:(?!\s*groupPolicyContainer)"
blacklist2 = EventCode="566" Message="Object Type:(?!\s*groupPolicyContainer)"
blacklist3 = EventCode=4673 ProcessName="*\\DesktopExtension.exe*"
renderXml=false
index=oswinsec
However even after restarting the splunk forwarder the events still appear. I verified one of the hosts has the correct inputs.conf. I have also tried
blacklist3 = EventCode=4673 ProcessName="C:\Program Files\WindowsApps\AD2F1837.myHP_28.52349.1300.0_x64__v10z8vjag6ke6\win32\DesktopExtension.exe""
Here is an example of the log/event:
Any tips?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, that should work.
blacklist = EventCode=4673 message="DesktopExtension\.exe"If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I see that the desktopexetension.exe is also in the message so would something like this work?
blacklist = EventCode=4673 message="DesktopExtension.exe"
Here is an example message:
A privileged service was called. Subject: Service: Server: Security Service Name: - Process: Process ID: 0x2fcc Process Name: C:\Program Files\WindowsApps\AD2F1837.myHP_26.52343.948.0_x64__v10z8vjag6ke6\win32\DesktopExtension.exe Service Request Information: Privileges: SeTcbPrivilege
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, that should work.
blacklist = EventCode=4673 message="DesktopExtension\.exe"If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
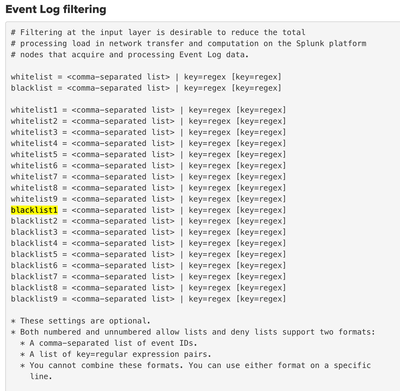
"ProcessName" is not a valid key for a blacklist setting. Valid keys are "Category, CategoryString, ComputerName, EventCode, EventType, Keywords, LogName, Message, OpCode, RecordNumber, Sid, SidType, SourceName, TaskCategory, Type, and User".
Also, the RHS must be a valid regular expression. A valid regex cannot begin with "*". If you're trying to specify a wildcard at the beginning and end of the match then there's no need - that's implied with most regexes.
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Did not know about the valid key entries. Thanks for sharing!
Came across this documentation after reading your comment.
https://docs.splunk.com/Documentation/Splunk/9.1.2/Data/MonitorWindowseventlogdata
Oof and this right in inputs.conf docs
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
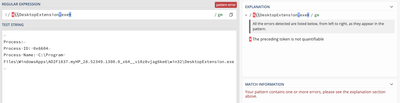
Give this a try
blacklist3 = EventCode="4673" Process_Name=".*\\DesktopExtension\.exe.*"From what I'm reading on Splunk docs it seems that it needs to be a valid regex to work.
This regex seems to match properly
The original regex you posted doesn't seem to valid according to regex101
Also noticed that the Key you posted "ProcessName" is different then the field I see extracted on windows data on my local machine which is extracted as "Process_Name" but maybe that is how it is coming over in your environment. If that is the case then maybe this could work.
blacklist3 = EventCode="4673" ProcessName=".*\\DesktopExtension\.exe.*"