Join the Conversation
- Find Answers
- :
- Splunk Administration
- :
- Getting Data In
- :
- Re: JSON Syntax highlighting by default
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
The syntax highlighting for JSON data (with INDEXED_EXTRACTIONS = JSON) is a nice feature. However, from what I can tell you have to click on each event you want to be syntax highlighted. In fact, twice really, as you usually have to click to "show all X lines", then "Show syntax highlighted".
Is there a way to set this as the for the default display mode?
Cheers,
Glenn
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You probably want KV_MODE = json in props.conf on the search head. That enables automatic search-time field extraction, and is independent of indexed extractions. Normally, if KV_MODE is on, regardless of whether indexed extractions are enabled, the data is JSON syntax highlighted.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
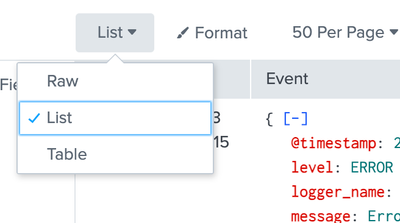
If anybody still facing this issues and could not figured out the solution.
In my case, I had to change view type.
You can see here there are three options to choose Raw, List, Table. If you want to set JSON syntax highlight by default, you should choose List view.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I am also facing this type of problem so can any one suggest me how to solve these problems.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Have you tried turning JSON pretty print off?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I know this thread is super old, but this is the only thing that came up when I was looking for an answer for the same problem. It turned out I had JSON pretty print on, so an event took up multiple lines. Once I turned pretty print off and each event took exactly one line, syntax highlighting was back on by default.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I know this is a very old question, but I ended up here when searching for a solution. In my case, I had two problems that were preventing the automatic syntax-highlighting. First, in some cases, we had "invalid" JSON. Specifically, we had a field that was duplicated (i.e. we had two "method" fields in our output). The second problem (that required setting "max lines" to "all lines" was that we were pretty-printing our JSON into the logs. This looked better when looking at the logs directly, but then Splunk only saw the first 5 lines (default Max Lines) and didn't syntax-highlight it unless we selected "all lines' for "max lines" in the "format" dropdown.
So, make sure the JSON is valid and that it's all printed on one line.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Bingo! That was my problem was well: had pretty print on, which meant each event took up multiple lines. Turning pretty print off fixed the default syntax highlighting. Thanks for the tip 🙂
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This helped me understand the issue I had - thanks. Then I found this and was able to remove the newline characters entirely:
https://answers.splunk.com/answers/111206/can-i-remove-blank-lines-in-my-event.html
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have the same problem, but oddly enough, only in JSON from certain hosts. From some of my hosts, I get syntax highlighting by default -- I didn't have to do anything -- and on other hosts, I have to click "Show all x lines," then click "Show syntax highlighted" before highlighting will display.
All the hosts seem to emit well-formed JSON. The only difference I can see at the moment is that the hosts that work (the ones that show syntax highlighting by default) have the timestamp as the first field. The hosts that don't work have the timestamp in the middle of the event. Does the timestamp field need to be first for some reason?
I've tried adding KV_MODE = json to the [default] stanza in props.conf, and that didn't fix the problem.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
In a custom dashboard, I was able to get JSON to display with syntax highlighting by setting maxLines to 0. (All Lines)
<event>
<title></title>
<search>
<query>*</query>
<earliest>0</earliest>
<latest></latest>
</search>
<option name="list.drilldown">full</option>
<option name="list.wrap">1</option>
<option name="maxLines">0</option>
<option name="raw.drilldown">full</option>
<option name="rowNumbers">0</option>
<option name="table.drilldown">all</option>
<option name="table.wrap">1</option>
<option name="type">list</option>
<option name="count">10</option>
<fields>["host","source","sourcetype"]</fields>
</event>
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You probably want KV_MODE = json in props.conf on the search head. That enables automatic search-time field extraction, and is independent of indexed extractions. Normally, if KV_MODE is on, regardless of whether indexed extractions are enabled, the data is JSON syntax highlighted.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Same problem here. I do have KV_MODE = json in my props.conf:
[source::/my/source/*]
KV_MODE = json
TRUNCATE = 100000
SHOULD_LINEMERGE = false
MUST_BREAK_AFTER = ($)
But the syntax highlighted by default is not working for me (it is available as a clickable option though)! Any ideas?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sorry, and I'm running Splunk v6.3.0