Getting Data In
×
Are you a member of the Splunk Community?
Sign in or Register with your Splunk account to get your questions answered, access valuable resources and connect with experts!
- Find Answers
- :
- Splunk Administration
- :
- Getting Data In
- :
- How to parse JSON with multiple array
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
cuongnguyen112
Engager
10-20-2019
09:07 PM
hi, i got data like this:
{
"source": "sadmin",
"sysinfo": {
"process_list": {
"56": {
"name": "nginx on",
"pid": 56,
"uid": 0,
"gid": 0
},
"57": {
"name": "nginx: worker process",
"pid": 57,
"uid": 33,
"gid": 33
},
}
}
}
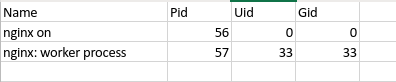
i need to create a table from these data like below:
could any one please help me !!
1 Solution
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
kamlesh_vaghela

SplunkTrust
10-20-2019
11:21 PM
@cuongnguyen112
Can you please try this?
YOUR_SEARCH | rename sysinfo.process_list.* as *
| eval field_name="",uid="",gid="",name="",pid=""
| foreach *.*
[ eval field_name= mvindex(split("<<FIELD>>","."),1),val=case(field_name=="pid",pid,field_name=="gid",gid,field_name=="uid",uid,1=1,name), {field_name}=if(val!="",val.",","").'<<FIELD>>']
| eval tmp=mvzip(mvzip(mvzip(split(name,","),split(pid,",")),split(uid,",")),split(gid,","))
| fields _time tmp | mvexpand tmp | eval name=mvindex(split(tmp,","),0),pid=mvindex(split(tmp,","),1),uid=mvindex(split(tmp,","),2),gid=mvindex(split(tmp,","),3)
| table name pid uid gid
Sample Search:
| makeresults
| eval _raw="{\"source\": \"sadmin\",\"sysinfo\": {\"process_list\": {\"56\": {\"name\": \"nginx on\",\"pid\": \"56\",\"uid\": \"0\",\"gid\": \"0\"},\"57\": {\"name\": \"nginx: worker process\",\"pid\": \"57\",\"uid\": \"33\",\"gid\": \"33\"},}}}"
| spath
| rename sysinfo.process_list.* as *
| eval field_name="",uid="",gid="",name="",pid=""
| foreach *.*
[ eval field_name= mvindex(split("<<FIELD>>","."),1),val=case(field_name=="pid",pid,field_name=="gid",gid,field_name=="uid",uid,1=1,name), {field_name}=if(val!="",val.",","").'<<FIELD>>']
| eval tmp=mvzip(mvzip(mvzip(split(name,","),split(pid,",")),split(uid,",")),split(gid,","))
| fields _time tmp | mvexpand tmp | eval name=mvindex(split(tmp,","),0),pid=mvindex(split(tmp,","),1),uid=mvindex(split(tmp,","),2),gid=mvindex(split(tmp,","),3)
| table name pid uid gid
Thanks
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
kamlesh_vaghela

SplunkTrust
10-20-2019
11:21 PM
@cuongnguyen112
Can you please try this?
YOUR_SEARCH | rename sysinfo.process_list.* as *
| eval field_name="",uid="",gid="",name="",pid=""
| foreach *.*
[ eval field_name= mvindex(split("<<FIELD>>","."),1),val=case(field_name=="pid",pid,field_name=="gid",gid,field_name=="uid",uid,1=1,name), {field_name}=if(val!="",val.",","").'<<FIELD>>']
| eval tmp=mvzip(mvzip(mvzip(split(name,","),split(pid,",")),split(uid,",")),split(gid,","))
| fields _time tmp | mvexpand tmp | eval name=mvindex(split(tmp,","),0),pid=mvindex(split(tmp,","),1),uid=mvindex(split(tmp,","),2),gid=mvindex(split(tmp,","),3)
| table name pid uid gid
Sample Search:
| makeresults
| eval _raw="{\"source\": \"sadmin\",\"sysinfo\": {\"process_list\": {\"56\": {\"name\": \"nginx on\",\"pid\": \"56\",\"uid\": \"0\",\"gid\": \"0\"},\"57\": {\"name\": \"nginx: worker process\",\"pid\": \"57\",\"uid\": \"33\",\"gid\": \"33\"},}}}"
| spath
| rename sysinfo.process_list.* as *
| eval field_name="",uid="",gid="",name="",pid=""
| foreach *.*
[ eval field_name= mvindex(split("<<FIELD>>","."),1),val=case(field_name=="pid",pid,field_name=="gid",gid,field_name=="uid",uid,1=1,name), {field_name}=if(val!="",val.",","").'<<FIELD>>']
| eval tmp=mvzip(mvzip(mvzip(split(name,","),split(pid,",")),split(uid,",")),split(gid,","))
| fields _time tmp | mvexpand tmp | eval name=mvindex(split(tmp,","),0),pid=mvindex(split(tmp,","),1),uid=mvindex(split(tmp,","),2),gid=mvindex(split(tmp,","),3)
| table name pid uid gid
Thanks
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
cuongnguyen112
Engager
10-20-2019
11:38 PM
you're my hero, exactly what i needed
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
kamlesh_vaghela

SplunkTrust
10-21-2019
12:27 AM
🙂 Glad to help you.
!! Happy Splunking !!
Get Updates on the Splunk Community!
Celebrating the Winners of the ‘Splunk Build-a-thon’ Hackathon!
We are thrilled to announce the winners of the Splunk Build-a-thon, our first-ever hackathon dedicated to ...
Why You Should Register for Splunk University at .conf25
Level up before .conf25 even begins
Splunk University is back in Boston, September 6–8, and it’s your chance ...
Building Splunk proficiency is a marathon, not a sprint
Building Splunk skills is a lot like training for a marathon. It’s about consistent progress, celebrating ...