- Splunk Answers
- :
- Splunk Administration
- :
- Getting Data In
- :
- How to integrate openCTI with Splunk?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How to integrate openCTI with Splunk?
Hi!
I'm currently working on a project where I aim to integrate the OpenCTI platform with Splunk in order to receive intelligence feeds, how can i configure the ingestion of this intelligence feeds ?
Any advice, tips, or resources you can provide will be highly appreciated
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Please I need the method if it is done with you
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @tuts ,
I’m a Community Moderator in the Splunk Community.
This question was posted 1 year ago, so it might not get the attention you need for your question to be answered. We recommend that you post a new question so that your issue can get the visibility it deserves. To increase your chances of getting help from the community, follow these guidelines in the Splunk Answers User Manual when creating your post.
Thank you!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
i am having a hard time integrating opencti into splunk, not sure if you have done it, can you help me
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
A bit of Googling and searching the OpenCTI web site turned up this connector: https://github.com/OpenCTI-Platform/connectors/tree/master/stream/splunk
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You are reading his request backwards. That git project is for SENDING TO OpenCTI. He (and I) need to RECEIVE FROM OpenCTI. I cannot find anything that does this.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you for your answers,
So there is no configuration to do in splunk platform for this connection
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'm not saying that. You may need to configure a sourcetype in props.conf for the data. With luck, the connector documentation will let you know. If the connector does not come with a Splunk props.conf file then you'll need to craft one yourself.
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you for your response,
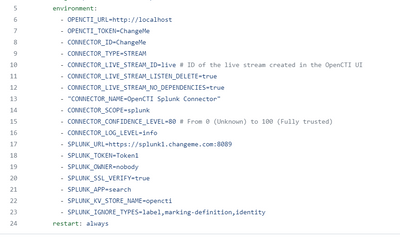
i checked the provided link, and i found that openCTI needs this information :
So what value will the variable "SPLUNK_TOKEN=Token1" and "SPLUNK_OWNER=nobody " take ?
And now do i still need to configure a sourcetype in props.conf for the data ?
NB: i checked the props.conf file and i found just the syslog configuration
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You will need to create a token for the connector to use. Go to Settings->Tokens for that.
I'm not sure what they expect for SPLUNK_OWNER. Try it with "nobody" for now.
The screenshot doesn't say if props are needed or not. The default syslog props may be sufficient, but you'll have to onboard some data to find out.
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
thank you ,
Well i tested the OpenCTI connector but the connection didn't work .
Do i need to set up a kv store before or maybe i need to configure HTTP Event Collector in order to integrate opencti to splunk.
i don't know also if this issues has a relation with REST API connection
The objective is to receive intelligence feeds from opencti platform in STIIX format to my splunk instance.
NB: - I don't have the splunk entreprise app that provide the threat intelligence management section
- I'm using the free trial
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The OpenCTI settings you showed earlier imply a KVStore is used and so must be created. I see no mention of HEC, however.
I think the best place to direct your questions is to the OpenCTI team.
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content