Are you a member of the Splunk Community?
- Find Answers
- :
- Splunk Administration
- :
- Getting Data In
- :
- Re: How do you search, by day, for the first and t...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How do you search, by day, for the first and the last user to log in and log off in a Windows event?
Good morning, I'm doing a search to bring users and their first log in of the day and their last log off.
I made the following query, but I can not get the first line of the 4624 and the last one of the 4636 in the same line.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@yassy ,
Give this a try
index="your index" day="your day field"
|stats earliest(eval(if(EventCode="4624",_time,null()))) as PrimerLogin,
last(eval(if(EventCode="4634 ",_time,null()))) as UltimoLogoff by User,day
What goes around comes around. If it helps, hit it with Karma 🙂
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
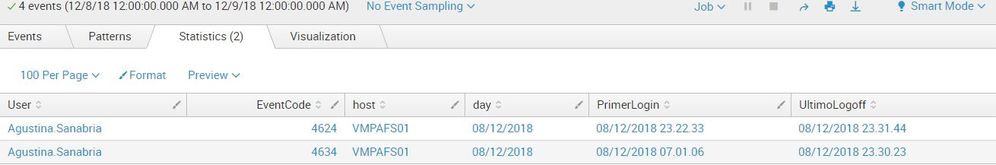
Tks finally i resolve it with this search
index=wineventlog (EventCode="4624" ) Account_Name!=AdminSp Account_Name!=AdminCitrix
| regex Account_Name!=".*\$"
| eval Day=strftime(_time,"%d/%m/%Y")
| eval User=mvindex(Account_Name,1)
| eval Time=strftime(_time,"%d/%m/%Y %H.%M.%S")
| stats earliest(Time) as PrimerLogin by User,Day
| join User,Day
[search
index=wineventlog (EventCode="4634" ) Account_Name!=AdminSp Account_Name!=AdminCitrix
| regex Account_Name!=".*\$"
| eval Day=strftime(_time,"%d/%m/%Y")
| eval User=Account_Name
| eval Time=strftime(_time,"%d/%m/%Y %H.%M.%S")
| stats latest(Time) as UltimoLogoff by User,Day
]
| stats values(PrimerLogin) as PrimerLogin,values(UltimoLogoff) as UltimoLogoff by User,Day
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@yassy , avoid join if possible. Wasn't the earlier search provided working?
What goes around comes around. If it helps, hit it with Karma 🙂