- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
BREAK_ONLY_BEFORE works but LINE_BREAKER automatically added
Can I configure BREAK_ONLY_BEFORE with this regex:
##################################################################|(pg-2 \| [a-zA-Z0-9._%-]* \| rc=0 >>)|(ss7-2 \| [a-zA-Z0-9._%-]* \| rc=0 >>)|(ss7-1 \| [a-zA-Z0-9._%-]* \| rc=0 >>)|(da-1 \| [a-zA-Z0-9._%-]* \| rc=0 >>)|(da-2 \| [a-zA-Z0-9._%-]* \| rc=0 >>)|(fs-3 \| [a-zA-Z0-9._%-]* \| rc=0 >>)|(fs-2 \| [a-zA-Z0-9._%-]* \| rc=0 >>)|(fs-1 \| [a-zA-Z0-9._%-]* \| rc=0 >>)|(om-1 \| [a-zA-Z0-9._%-]* \| rc=0 >>)|(pg-1 \| [a-zA-Z0-9._%-]* \| rc=0 >>)|(om-2 \| [a-zA-Z0-9._%-]* \| rc=0 >>)|(mms-1 \| [a-zA-Z0-9._%-]* \| rc=0 >>)|(mms-2 \| [a-zA-Z0-9._%-]* \| rc=0 >>)
and SHOULD_LINEMERGE to true?
My problem is , when I configure this, Splunk automatically added the regex that I have specified in BREAK_ONLY_BEFORE as LINE_BREAKER. So the result is not what I want. I want to keep the regex specified in the event. I do not want the LINE_BREAKER because it will remove the regex specified. Does anyone know what I should do for this?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I presume you're using the GUI to make these settings. Have you tried editing the props.conf file directly?
The LINE_BREAKER attribute discards the contents of the first capture group, which can be empty. Therefore, this should be equivalent to your BREAK_ONLY_BEFORE setting:
()##################################################################|(pg-2 \| [a-zA-Z0-9._%-]* \| rc=0 >>)|(ss7-2 \| [a-zA-Z0-9._%-]* \| rc=0 >>)|(ss7-1 \| [a-zA-Z0-9._%-]* \| rc=0 >>)|(da-1 \| [a-zA-Z0-9._%-]* \| rc=0 >>)|(da-2 \| [a-zA-Z0-9._%-]* \| rc=0 >>)|(fs-3 \| [a-zA-Z0-9._%-]* \| rc=0 >>)|(fs-2 \| [a-zA-Z0-9._%-]* \| rc=0 >>)|(fs-1 \| [a-zA-Z0-9._%-]* \| rc=0 >>)|(om-1 \| [a-zA-Z0-9._%-]* \| rc=0 >>)|(pg-1 \| [a-zA-Z0-9._%-]* \| rc=0 >>)|(om-2 \| [a-zA-Z0-9._%-]* \| rc=0 >>)|(mms-1 \| [a-zA-Z0-9._%-]* \| rc=0 >>)|(mms-2 \| [a-zA-Z0-9._%-]* \| rc=0 >>)If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Do you know where is the props.conf? I have tried to find it but I failed to find it.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
There should be more than one props.conf file on most systems. One of them is always $SPLUNK_HOME/etc/system/default/props.conf, but it must NEVER be modified.
Other props.conf files can be in $SPLUNK_HOME/etc/system/local or $SPLUNK_HOME/etc/apps/*/default or $SPLUNK_HOME/etc/apps/*/local. There are other locations for deployment servers and for SH and indexer clusters. The location that is right for you depends on your architecture and the instance that is to load the file.
One way to find an existing props.conf file is with btool. Run this command
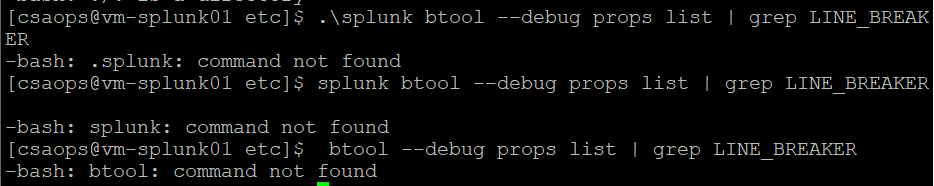
splunk btool --debug props list | grep LINE_BREAKERThe --debug option shows the name of the file the setting came from and grep is used to make the output less verbose.
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Why it said the command not found?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The command "splunk" was not found in your $PATH setting. Either update $PATH or qualify the command.
export PATH=$PATH:/opt/splunk/bin/opt/splunk/bin/splunk btool --debug props list | grep LINE_BREAKERThis is not unique to Splunk, but the way the OS works.
If this reply helps you, Karma would be appreciated.