Join the Conversation
- Find Answers
- :
- Splunk Administration
- :
- Getting Data In
- :
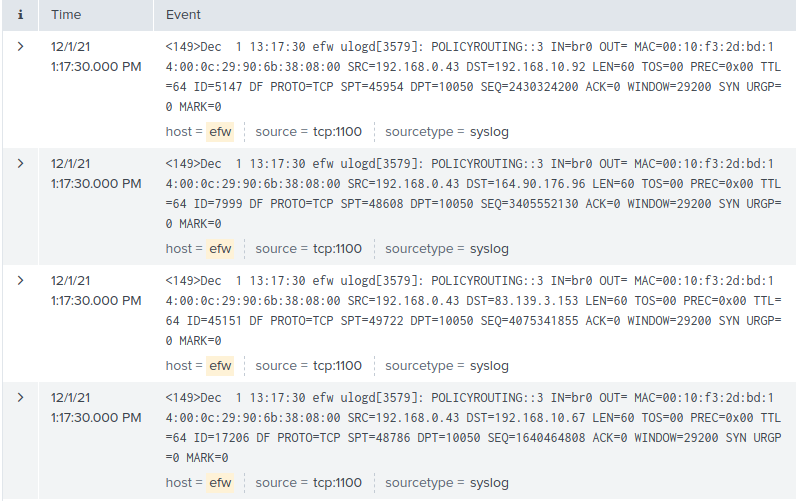
- A number is added to log entries collected through...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
I'm collecting syslog events from network to a dedicated universal forwarder using a TCP input on forwarder.
In my Splunk installation I get all the syslog entries, but there's a number in angled brackets (<149>, for example) added to the beginning of every log entry added to Splunk index. That number is not always <149>, it changes, but I cannot find the logic behind those changes.
That angled bracketed number does not allow to implement correct field extraction.
So my question is: how do I get rid of that number in angled brackets? Shall it be done on forwarder?
I'm sorry if my question is stupid, or is well-covered in documentation, I'm relatively new to Splunk and learning now.
Thank you!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi
that value is combination of syslog facility and priority. You could see it e.g. from here 6.2.1 (RFC)
If you don't need it you could remove it on Indexer (actually first Full Splunk Enterprise instance e.g. HF in your flow) with props.conf with sed or using also transforms.conf if you want do something more at same time.
If you are using UDP (don't use ;-), there is parameter in inputs.conf which can manage it. But as we know udp always lost some packets, it's not good idea to use it. Actually it will be best to use some real syslog server and then use UF for reading events from file instead of receiving those directly with UF/HF.
r. Ismo
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi
that value is combination of syslog facility and priority. You could see it e.g. from here 6.2.1 (RFC)
If you don't need it you could remove it on Indexer (actually first Full Splunk Enterprise instance e.g. HF in your flow) with props.conf with sed or using also transforms.conf if you want do something more at same time.
If you are using UDP (don't use ;-), there is parameter in inputs.conf which can manage it. But as we know udp always lost some packets, it's not good idea to use it. Actually it will be best to use some real syslog server and then use UF for reading events from file instead of receiving those directly with UF/HF.
r. Ismo
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you so much, @isoutamo for your reply!
I've opened TCP receiver on TCP/1100 (I already have lessons learned with UDP 🙂 ) on universal forwarder and was collecting logs from it.
Will follow your advice.
Thank you again!