Join the Conversation
- Find Answers
- :
- Splunk Administration
- :
- Deployment Architecture
- :
- Re: How do you find the disabled user along with t...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How do you find the disabled user along with the availability of their respective adm-user?
We have 2 types of accounts in our organization
- user
- adm-user
I can find the disabled users in the organization, but I need to find adm account of disabled user.
Note: we have 40% of users in the organization those have their adm accounts
So, to find the adm accounts for the accounts that are disabled, we need to manually disable the ADM accounts
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
hi @deepak007 ,
Did you have a chance to check out afurrowgtri's answer? If it worked, please resolve this post by approving it! If your problem is still not solved, keep us updated so that someone else can help ya.
Thanks for posting!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You have many options for tackling this. Best practice would be to set up SA-LDAPSearch, configure it for your domain, and write a query using the ldapsearch command with an appropriate filter. Also, the Splunk Add-on for Microsoft Active Directory can help you ingest this data and map your domain. These solutions require some modest effort to set up and properly utilize.
Alternatively, if your search head is running Windows and is joined to the domain you want to search, I would suggest writing a simple one-liner scripted input in PowerShell to fetch all users, their SID, status, and any other information you may be interested in. Test the script first though, as I'm a little rusty. This has the added benefit that you're now indexing the information, so you can audit it for changes over time. Adjust the schedule to a frequency your organization is comfortable with.
Put a stanza like this in your inputs.conf:
[powershell://GetADUsers]
script = Get-ADUser -Filter * -SearchBase "OU=Finance,OU=UserAccounts,DC=FABRIKAM,DC=COM" -Properties SamAccountName,Name,SID,Enabled | Select SamAccountName,Name,SID,Enabled
schedule = 0 */5 * * *
sourcetype = Domain:Users
index = msad
Perhaps write a scheduled search to maintain a lookup table for the accounts. This way you can use it more efficiently in other searches:
index="msad" sourcetype="Domain:Users" SID="*"
| dedup SID sortby -_indextime
| table SamAccountName Name SID Enabled
| outputlookup adUsers.csv
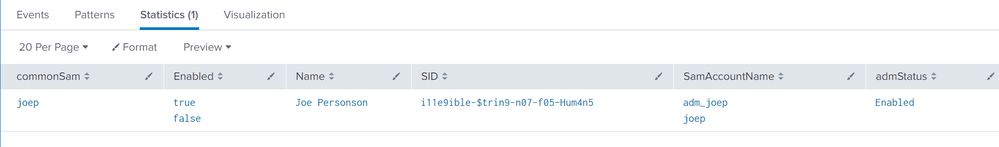
And finally, however you choose to get the necessary data, write a search using some kind of logic to pair the regular and ADM accounts together. Be sure to customize the admStatus eval with your ADM account naming convention. The goal is to normalize the SamAccountName field and find matching ADM accounts, unless you have another method of pairing them (email? a note field or custom property in AD?). There are many ways to write this search, and you may wish to do additional iterations of replace() on the SamAccountName to remove spaces or other characters that might cause a false negative.
| inputlookup adUsers.csv
| eval commonSam=replace(SamAccountName,"adm_","")
| eval admStatus=case(match(SamAccountName,"^adm_") AND Enabled=="true","Enabled")
| stats list(*) AS * by commonSam
| search admStatus="Enabled" AND Enabled="false"
This will produce a statistics table like below, showing you which disabled users still have active ADM accounts:
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@afurrowgtri How do handle a multi valued filed. For example if a field is enclosed in { }. Say a filed called MemberOf: { CN=(cndata) (otherdata) }. The filed does not populate in the export. It exports like this MemberOf="System.Object[]" with no data.
Thanks for your help.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks very much for the help,
Appreciate your effort
but we have little problem, we do not have access to input.conf
can the same be done by a search query