Join the Conversation
- Find Answers
- :
- Splunk Administration
- :
- Deployment Architecture
- :
- Re: Cluster Map: Problem with Zoom & Center in Das...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Good day fellow Splunkers!
I'm having a small trouble with a Cluster Map in one of my dashboards which is driving me crazy!!! And I'm thinking maybe it is a bug, because it doesn't make any sense. Here is my problem:
I have a Cluster Map, which I want to show in a custom location with a custom zoom. For doing that, I defined the cluster maps options like this:
<option name="mapping.map.center">($lat$, $lon$)</option>
<option name="mapping.map.zoom">7</option>
Being defined and obtained my custom tokens "lat" & "lon" on a previous search, like this:
<search id="bbase">
<query>index="fomento" sourcetype=secure failed ip_src=$ip_src$ | iplocation ip_src | table ip_src lat lon | head 1</query>
<finalized>
<condition match="'job.resultCount' != 0">
<set token="lat">$result.lat$</set>
<set token="lon">$result.lon$</set>
</condition>
</finalized>
</search>
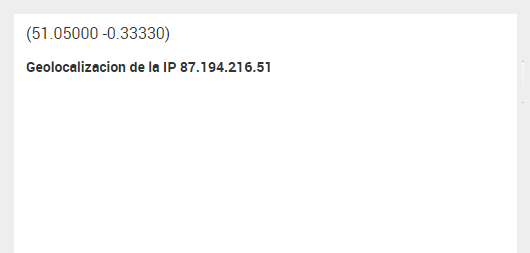
The thing is, the first time I access this dashboard, the Cluster Map shows nothing. However, I can see the values of my lat and lon custom tokens on the panel title (I put them there, like $lat$, $lon$ to check the values):
But! (And here comes the magic), if I go to edit > source > cancel in my dashboard, suddenly... TADAAAAA!!! The Cluster map is shown with my custom options and tokens!!!
Does anybody why this is happening? This approach is the only way I found to do this (I couldn't with do it in other way). Is this a Splunk bug, maybe?
I'm using Splunk 7, btw.
Thank you very much!
Best regards
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@faguilar, you have wrong tokens for latitude and longitude fields generated in results via iplocation command. They should be $result.latitude$ and $result.longitude$. While this should fix your issue I recommend following changes.
Changes to Search:
It is better to perform stats first followed by iplocation to enrich ip_src (in your case, with the following search iplocation will be applicable for single row). Finally use sum() for the field aggregated by stats in our case sum(Total).
index="fomento" sourcetype=secure failed ip_src=$ip_src$
| stats count as Total by ip_src
| iplocation ip_src
| geostats sum(Total) as Total by ip_src
Refer to documentation:
http://docs.splunk.com/Documentation/Splunk/latest/SearchReference/Geostats#Usage
http://docs.splunk.com/Documentation/Splunk/latest/SearchReference/Lookup#Optimizing_your_lookup_sea...
Changes to Search Event Handler
Actual fields in the table after iplocation are latitude and longitude, hence the tokens should be set through $result.latitude$, $result.longitude$
<done>
<condition match="'job.resultCount' == 0">
<set token="lat">0</set>
<set token="lon">0</set>
<set token="zoom">2</set>
</condition>
<condition>
<set token="lat">$result.latitude$</set>
<set token="lon">$result.longitude$</set>
<set token="zoom">7</set>
</condition>
</done>
Changes in Map Simple XML Configuration:
Set Map Center as Well as Zoom based on tokens. Zoom=7 if search returns latitude and longitude.
<option name="mapping.map.center">($lat$,$lon$)</option>
<option name="mapping.map.zoom">$zoom$</option>
PS:
I have added zoom token as well for No Results found scenario, where it should display the entire map i.e. zoom=2 with center at actual center of the globe i.e. (0,0).
For debug purpose always print the token values somewhere in your dashboard for initial development/testing like you have used $ip_src$ in Map <title>, similarly if you would have printed $lat$ and $lon$ you would have figured out that the tokens were null, since $result.lat$ and $result.lon$ did not return any value. Remove additional debug token values once they are tested to be working 🙂
Please try out the changes and confirm.
| makeresults | eval message= "Happy Splunking!!!"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@faguilar even in 2020, with Splunk 7.3.4, facing the same problem! Did you figure out the issue or moved on with (0,0) for lat and long?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi!
I had to move on using (0,0), sorry I couldn't help
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @niketnilay, and thank you again for your support.
I've tried all the steps you told me, but unfortunately, it still doesn't work... The same problem again, the first time the panel is shown in blank, it only loads the map after going into the dashboard source.
I've tried to access using Firefox and Edge instead of Chrome, but the behavior is the same.
Could you check it in your own Splunk instance? Because I don't know what else to do... ;( And I'm thinking that maybe this is a Splunk bug...
Thank you again!
Best regards
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@faguilar, you have wrong tokens for latitude and longitude fields generated in results via iplocation command. They should be $result.latitude$ and $result.longitude$. While this should fix your issue I recommend following changes.
Changes to Search:
It is better to perform stats first followed by iplocation to enrich ip_src (in your case, with the following search iplocation will be applicable for single row). Finally use sum() for the field aggregated by stats in our case sum(Total).
index="fomento" sourcetype=secure failed ip_src=$ip_src$
| stats count as Total by ip_src
| iplocation ip_src
| geostats sum(Total) as Total by ip_src
Refer to documentation:
http://docs.splunk.com/Documentation/Splunk/latest/SearchReference/Geostats#Usage
http://docs.splunk.com/Documentation/Splunk/latest/SearchReference/Lookup#Optimizing_your_lookup_sea...
Changes to Search Event Handler
Actual fields in the table after iplocation are latitude and longitude, hence the tokens should be set through $result.latitude$, $result.longitude$
<done>
<condition match="'job.resultCount' == 0">
<set token="lat">0</set>
<set token="lon">0</set>
<set token="zoom">2</set>
</condition>
<condition>
<set token="lat">$result.latitude$</set>
<set token="lon">$result.longitude$</set>
<set token="zoom">7</set>
</condition>
</done>
Changes in Map Simple XML Configuration:
Set Map Center as Well as Zoom based on tokens. Zoom=7 if search returns latitude and longitude.
<option name="mapping.map.center">($lat$,$lon$)</option>
<option name="mapping.map.zoom">$zoom$</option>
PS:
I have added zoom token as well for No Results found scenario, where it should display the entire map i.e. zoom=2 with center at actual center of the globe i.e. (0,0).
For debug purpose always print the token values somewhere in your dashboard for initial development/testing like you have used $ip_src$ in Map <title>, similarly if you would have printed $lat$ and $lon$ you would have figured out that the tokens were null, since $result.lat$ and $result.lon$ did not return any value. Remove additional debug token values once they are tested to be working 🙂
Please try out the changes and confirm.
| makeresults | eval message= "Happy Splunking!!!"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @niketnilay and thank you again for your help!
I followed all the steps you told me and it looks like the behaviour is the same: the panel stays in blank, and it loads properly after digging into the dashboard's source.
I was thinking about maybe it was a problem of the browser (I'm using Google Chrome). But I checked with Firefox and Edge and the behaviour is the same.
However, I just discovered something weird by accident. When I hit the dashboard to open the drilldown, if I wait like, 10 seconds without open the new tab, after that time, it looks like the panel loads correctly!
Really, this is driving me crazy, becuase I don't know where "the problem" (if any) is, and how to solve it.
Could you check in your local instance for this same behaviour?
Thank you very much!
Regards
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@faguilar, I was able to recreate your issue only when the latitude and longitude tokens were not getting set.
However, my query was on an inputlookup where I pulled one few records. So performance might have been better.
You can try to change from <done> to <progress> which will pass on the $result.fieldname$ token/s as soon as they are available rather than waiting for the search to complete. This might improve performance a bit. But actual delay might come in your search if you do iplocation first and then geostats. Run your search in Splunk Search window. In the Job Inspector validate as to how long it takes for the search to resturn results.
I am using Splunk 7 and Google Chrome, but like I said I might not have put realtime production data kind of load as I performed a lookup in the sample geomap data provided with Splunk Dashboard Examples app. Do share your current query if you are still seeing delay.
| makeresults | eval message= "Happy Splunking!!!"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@niketnilay, it looks like the preformance is better with <done> than with <progress> so i think I'll be using that. And I will dig deeper onto this issue, checking the job inspector, I'll update if I find something.
I'm marking your answer as correct, because I think is the best approach I can obtain.
Again, thank you very much for your help!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Anytime, do let us know if results do not turn out to be convincing 🙂
| makeresults | eval message= "Happy Splunking!!!"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@faguilar, <finalized> search event handler was deprecated from Splunk Enterprise 6.5 onward. Try to use <done>, instead. (You can also use <progress>, refer to Search Event Handler to decide which one you require: http://docs.splunk.com/Documentation/Splunk/latest/Viz/EventHandlerReference#Search_event_handlers).
Coming back to your query, you can improve its performance a lot by putting | head 1 right after your base search since you are only interested in the latest event in your data. Just try the following search instead and you will be surprised with the time this takes vs your original query (validate differences in Job Inspector for each search)
index="fomento" sourcetype=secure failed ip_src=$ip_src$
| head 1
| iplocation ip_src
| table ip_src lat lon
Please validate and confirm if it works for you.
| makeresults | eval message= "Happy Splunking!!!"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @niketnilay , thank you very much for your answer.
None of your two approaches ( <done> nor <progress> ) worked for me. The behaviour of the dashboard is the same with both of them. The first time, it shows a blank panel, but it loads the map when I hit edit > source > cancel.
Can you check out in your splunk instance for the same behaviour? The data I'm using is the one for the Splunk tutorial, I just changed the index's name.
I was thinking, maybe it has something to do with the order of the map option's definitions? Mine are these:
<title>Geolocalizacion de la IP $ip_src$</title>
<search>
<query>index="fomento" sourcetype=secure failed ip_src=$ip_src$ | iplocation ip_src | geostats count by ip_src</query>
<earliest>1509922800</earliest>
<latest>1510743600</latest>
<sampleRatio>1</sampleRatio>
</search>
<option name="drilldown">none</option>
<option name="mapping.choroplethLayer.colorBins">5</option>
<option name="mapping.choroplethLayer.colorMode">auto</option>
<option name="mapping.choroplethLayer.maximumColor">0xDB5800</option>
<option name="mapping.choroplethLayer.minimumColor">0x2F25BA</option>
<option name="mapping.choroplethLayer.neutralPoint">0</option>
<option name="mapping.choroplethLayer.shapeOpacity">0.75</option>
<option name="mapping.choroplethLayer.showBorder">1</option>
<option name="mapping.data.maxClusters">100</option>
<option name="mapping.legend.placement">bottomright</option>
<option name="mapping.map.center">($lat$, $lon$)</option>
<option name="mapping.map.panning">1</option>
<option name="mapping.map.scrollZoom">1</option>
<option name="mapping.map.zoom">7</option>
<option name="mapping.markerLayer.markerMaxSize">50</option>
<option name="mapping.markerLayer.markerMinSize">10</option>
<option name="mapping.markerLayer.markerOpacity">0.8</option>
<option name="mapping.showTiles">1</option>
<option name="mapping.tileLayer.maxZoom">7</option>
<option name="mapping.tileLayer.minZoom">0</option>
<option name="mapping.tileLayer.tileOpacity">1</option>
<option name="mapping.type">marker</option>
<option name="refresh.display">progressbar</option>
<option name="trellis.enabled">0</option>
<option name="trellis.scales.shared">1</option>
<option name="trellis.size">medium</option>
</map>
Thank you again!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
the issue is still happening in the current version of splunk.
<option name="mapping.map.center">($lat$,$lon$)</option>
Solution from @faguilar worked , on the other hand how long does it take to fix an issue reported in 2017 and it its 2021 end.
click cancel
so now instead if the a blank right map , it all works click on japan and it can see the right map center and zoom to jp lat lon.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-29-2022
I stumbled upon this splunk answer from a google search as I was also curious how to do this in splunk. It's quite unfortunate i'm having the same issue as mentioned as above about the white panel. I'm on Splunk version 9.0.1. Is this really a bug in splunk or does the panel not like some of the syntax we are offering? It's odd either way as I'd expect an error if there was bad syntax or for splunk to recognized and fix the bug giving it's been so long.
I want to take time out and thank @niketn For his hard work/ provided solution on this problem. I think what he's mentioned has been shadowed due to the bug or whatever this is.
I'm unsure if he is still active, or if any of you have been successful in finding a work around. i'd be curious to know what it is? I'd like to use in production but cannot if we have to click edit, cancel each time. I'm hoping there's a trick or workaround to get by as the provided answer works beautifully when it works.
When I got it working i was so happy, but much like most of you came back to notice it suddenly stopped working. Such a let down because i struggled for hours thinking i must of fat fingered some syntax.
Thanks for the feedback
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Has anyone found a solution or a work around for this problem?
I'm having the same issue
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Facing the same issue ☹️
Any update?