Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Dashboards & Visualizations
- :
- Re: Unable to extract fields from package source t...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
I'm trying to create a report that has information about all the hosts with the kernel version and OpenSSL version and SSH version. The package.sh (sourcetype=package)script on the Splunk_TA_*nix app fetches all the information but the issue is I'm not able to extract fields from the sourcetype=package.Any help is appreciated
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I just try with my lab env and here this works as expected.
index=os_unix* sourcetype=package NAME IN (openssh*, kernel*)
| table NAME VERSION RELEASE
| dedup NAME VERSION RELEASEI have installed TA nix on source system and also on my SH.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you so much for the reply @gcusello and @isoutamo .
Please find the sample logs.
NAME VERSION RELEASE ARCH VENDOR GROUP
initscripts 10.00.18 1.el8 x86_64 Red Hat, Inc. Unspecified
fuse 2.9.7 16.el8 x86_64 Red Hat, Inc. Unspecified
libattr 2.4.48 3.el8 x86_64 Red Hat, Inc. Unspecified
xmlsec1-openssl 1.2.25 4.el8 x86_64 Red Hat, Inc. Unspecified
lua 5.3.4 12.el8 x86_64 CentOS Development/Languages
zip 3.0 23.el8 x86_64 Red Hat, Inc. Applications/Archiving
libidn2 2.2.0 1.el8 x86_64 Red Hat, Inc. Unspecified
popt 1.18 1.el8 x86_64 Red Hat, Inc. System Environment/Libraries
nimsoft-robot 9.33 1 x86_64 CA Technologies System/Daemons
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Anu,
did you extracted the logs?
if yes, you can use the search from @isoutamo, if not, you can add to this search a regex extraction:
index=os_unix* sourcetype=package NAME IN (openssh*, kernel*)
| rex "^(?<NAME>[^ ]+)\s+(?<VERSION>[^ ]+)\s+(?<RELEASE>[^ ]+)\s+"
| table NAME VERSION RELEASE
| dedup NAME VERSION RELEASECiao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@isoutamo Can you please help
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi
can you post what you have already try and also part of sample package events?
r. Ismo
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I just try with my lab env and here this works as expected.
index=os_unix* sourcetype=package NAME IN (openssh*, kernel*)
| table NAME VERSION RELEASE
| dedup NAME VERSION RELEASEI have installed TA nix on source system and also on my SH.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Anu,
if you don't have the NAME field the main search will always not have results.
Anyway, good for you, see next time!
Ciao and happy splunking
Giuseppe
P.S.: Karma Points are appreciated by all the contributors 😉
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
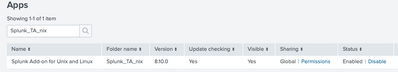
Have you installed TA..nix also on your search head and check that i5 has shared globally?
Your index is probably something else than os_unix*? If you don’t know the name try
index=* sourcetype=package system OR openssh If you haven’t have TA…nix installed, you should install it onto SH too and share it globally. That will enable this and other field extractions, tag and eventtypes to your use.
Another option is use that rex which @gcusello predented.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @isoutamo ,
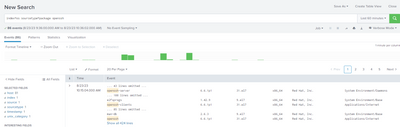
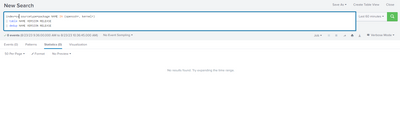
I have installed the TA*nix app on search heads as well,my index is os.I can see the results when i do the basic search index=* sourcetype=package but when i add NAME IN i dont see any results.Attached the screenshots for reference.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
And you have check that it's sharing is Global and status enabled?
When I look your output, it shows that your onboarding is not working correctly. Your query should return something like this
Please check that you have also this Splunk_TA_nix installed on your UF + Indexer / first full enterprise instance counting from UF.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Anu Can you double check the index name which you used while configuring this add-on?
if the index name is correct, give index=* and see if it fetches any results.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Roy_9 ,
Yes i do see results when i do the basic search with index and sourcetype .see above comment for more details.
Thanks
Anu