Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Dashboards & Visualizations
- :
- Time token to reflect user logins restricted by dr...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Time token to reflect user logins restricted by dropdowns
Hey guys,
Slightly new to Splunk, I have done a few searches in my time however, I am currently stuck on dropdowns. I have a search that is dependent on 3 dropdown inputs 2 of which are closely related to each other. 2 of which are my main concern.
To put it simply I have 1 dropdown entry which is the stand "Time" input and a second one which is "Username". What I want to be able to do is restrict the search of usernames based on what time frame the user enters on the "Time" input. I just cannot seem to get it to work and the token $time$ I have no way of entering this in?
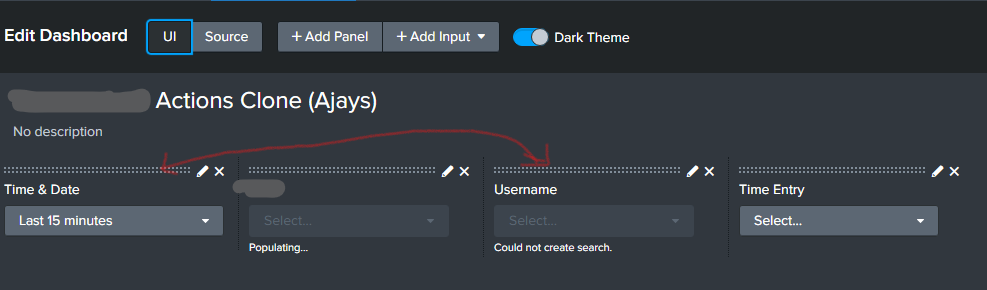
See below the code and screenshot to provide context. Please ask any questions that might assist in me solving this. I've tried also adding in a premade time entry input panel although I'd prefer to use the default due to more presets.
<form theme="dark">
<label>HealthRoster Actions Clone (Ajays)</label>
<search id="base_search">
<query>sourcetype=iis | table a_action,a_action_type,cs_User_Agent,a_module,a_request,a_process_action,a_module_detail,a_request_type,app,LHD,cs_username, _time
</query>
</search>
<fieldset submitButton="false" autoRun="false">
<input type="time" token="date" searchWhenChanged="false">
<label>Time & Date</label>
<default>
<earliest>-15m</earliest>
<latest>now</latest>
</default>
</input>
<input type="dropdown" token="LHD" searchWhenChanged="true">
<label>LHD</label>
<search base="base_search">
<query>| stats count by LHD</query>
</search>
<fieldForLabel>LHD</fieldForLabel>
<fieldForValue>LHD</fieldForValue>
</input>
<input type="dropdown" token="username" searchWhenChanged="true">
<label>Username</label>
<fieldForLabel>username</fieldForLabel>
<fieldForValue>cs_username</fieldForValue>
<search base="base_search">
<query>| search LHD=$LHD$ | stats count by cs_username</query>
</search>
</input>
<input type="dropdown" token="time">
<label>Time Entry</label>
<choice value="-30m@m">Last Half Hour</choice>
<choice value="-60m@m">Last 1 hour</choice>
<choice value="-240m@m">Last 4 hours</choice>
<choice value="-24h">Last 24 hours</choice>
<choice value="-48h">Last 2 days</choice>
<choice value="-10d@d">Last 10 days</choice>
</input>
</fieldset>
<row>
<panel>
Thanks
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Bassik ,
Token for your time input is date as per the xml entry and you haven't used in any of the searches.
<input type="time" token="date" searchWhenChanged="false">
You have to use this token in your base search to restrict the search to the time input. Otherwise the search will run for the default time window.
Try adding below to your base search
<search id="base_search">
<query>sourcetype=iis | table a_action,a_action_type,cs_User_Agent,a_module,a_request,a_process_action,a_module_detail,a_request_type,app,LHD,cs_username, _time
</query>
<earliest>$date.earliest$</earliest>
<latest>$date.latest$</latest>
</search>
Also please consider optimizing your base search. Please have a look at the reference for best practices
https://docs.splunk.com/Documentation/Splunk/8.0.3/Viz/Savedsearches#Use_a_transforming_base_search
What goes around comes around. If it helps, hit it with Karma 🙂