Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Dashboards & Visualizations
- :
- Search event handlers in splunk dashboard
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Search event handlers in splunk dashboard
Hi Team,
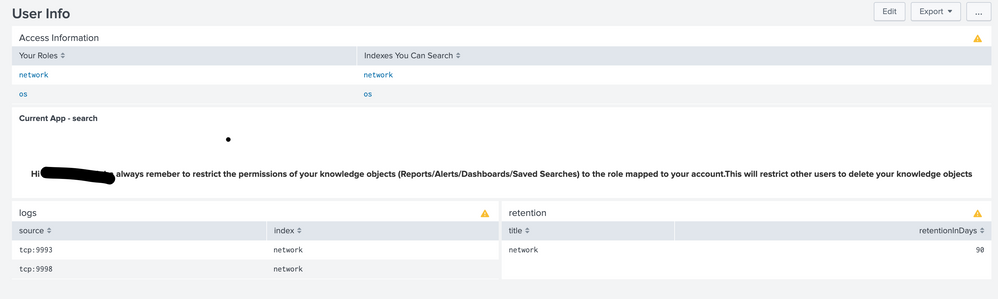
Im working on a user dashboard which gives some information about the metadata info about their access/logs/retention etc using rest queries.
I need some help on how to use Search event handlers token as it is considering only one value.I need all the results to be passed as token in the other search queries.
In the attached screenshot, under logs and retention panels , data is only being displayed for network index and not os index.So I need a help on getting os index info in logs and retention panels.
Thank you.
<dashboard>
<label>User Info</label>
<search>
<query>| rest /services/authentication/current-context splunk_server=local | fields roles
| mvexpand roles
| join type=left roles
[ rest /services/authorization/roles splunk_server=local
| table title srchIndexesAllowed
| rename title as roles]
| makemv srchIndexesAllowed tokenizer=(\S+)
| fillnull value=" "
| mvexpand srchIndexesAllowed | table srchIndexesAllowed</query>
<earliest>-60m@m</earliest>
<latest>now</latest>
<progress>
<set token="title">$result.srchIndexesAllowed$</set>
</progress>
</search>
<row>
<panel>
<title>Access Information</title>
<table>
<search>
<query>| rest /services/authentication/current-context splunk_server=local | fields roles
| mvexpand roles
| join type=left roles
[ rest /services/authorization/roles splunk_server=local
| table title srchIndexesAllowed
| rename title as roles]
| makemv srchIndexesAllowed tokenizer=(\S+)
| fillnull value=" "
| mvexpand srchIndexesAllowed
| stats values(*) as * by roles
| rename roles as "Your Roles", srchIndexesAllowed as "Indexes You Can Search"</query>
</search>
</table>
</panel>
</row>
<row>
<panel>
<single>
<title>Current App - $env:app$</title>
<search>
<query>| makeresults|eval message="Hi $env:user$ always remeber to restrict the permissions of your knowledge objects (Reports/Alerts/Dashboards/Saved Searches) to the role mapped to your account.This will restrict other users to delete your knowledge objects"</query>
<earliest>$earliest$</earliest>
<latest>$latest$</latest>
</search>
<option name="refresh.display">progressbar</option>
</single>
</panel>
</row>
<row>
<panel>
<title>logs</title>
<table>
<search>
<query>|rest /services/data/indexes count=0
| dedup title | fields title | map [|metadata type=sources index="$title$" | eval type="$title$"] maxsearches=1000
| stats values(type) AS index by source | sort source</query>
<earliest>-24h@h</earliest>
<latest>now</latest>
</search>
<option name="drilldown">none</option>
<option name="refresh.display">progressbar</option>
</table>
</panel>
<panel>
<title>retention</title>
<table>
<search>
<query>| rest splunk_server=* /services/data/indexes
| join type=outer $title$ [
| rest splunk_server=$title$ /services/data/indexes-extended
]
| search title=$title$
| eval retentionInDays=frozenTimePeriodInSecs/86400
| table title retentionInDays</query>
<earliest>-24h@h</earliest>
<latest>now</latest>
</search>
<option name="drilldown">none</option>
<option name="refresh.display">progressbar</option>
</table>
</panel>
</row>
</dashboard>
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @isoutamo I changed it and working .Can you help me fixing the retention panel.Thanks
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Basically this way:
| rest splunk_server=local /services/data/indexes
| join type=outer title [
| rest splunk_server=local /services/data/indexes-extended
]
| dedup title
| eval retentionInDays=frozenTimePeriodInSecs/86400
| table title retentionInDaysJust switch local to $title$ if that is list of our peers or use splunk_server=* for all peers.
r. Ismo
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This query is showing up the data for all indexes , but I want only those 2 indexes for which this roles has access to.I just need the data for those 2 indexes which are populating under access information panel.Thanks
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Maybe this helps you? You must add input to give user's account or use that $env:user$.
| rest /services/authentication/users splunk_server=*
| search title!=admin
| table title roles
| rename title as user
| rename roles as title
| search user=$env:user$
| mvexpand title
| join type=left max=0 title
[| rest /services/authorization/roles splunk_server=*
| table title srchInd*
| eval indexes=mvappend(srchIndexesAllowed,srchIndexesDefault)
| table title indexes
| mvexpand indexes
| dedup title indexes
| eval indexes_orig=indexes
| join indexes max=0 type=left
[| rest /services/data/indexes
| stats count by title
| table title
| eval indexes=if(match(title,"^_"),"_*","*")
| join type=outer title
[| rest splunk_server=* /services/data/indexes-extended]
| rename title as indexes_new]
| eval indexes=if(indexes_orig!=indexes_new,indexes_new, indexes_orig)
| table title indexes frozenTimePeriodInSecs]
| rename user as Username title as Group indexes as Index
| dedup Index
| eval retentionInDays=frozenTimePeriodInSecs/86400
| table Index retentionInDaysr. Ismo
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@isoutamo Its returning on the Index column and retention period column is empty.Can you please check why its not working.Thank you
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It seems to have issues when using in a distributed environment. In a single instance it works. Let's wait and I will fix it, it needs still some fine-tuning before it's ready to publish.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Here is the fixed version which works on both single instance and multisite cluster with shc.
| rest /services/authentication/users splunk_server=*
| search title!=admin
| table title roles
| rename title as user
| rename roles as title
| search user=<YOUR USER ACCOUNT HERE / $env:user$ if run from dashboard>
| mvexpand title
| join type=left max=0 title
[| rest /services/authorization/roles splunk_server=*
| table title srchInd*
| eval indexes=mvappend(srchIndexesAllowed,srchIndexesDefault)
| table title indexes
| mvexpand indexes
| dedup title indexes
| eval indexes_orig=indexes
| join indexes max=0 type=left
[| rest /services/data/indexes splunk_server=*
| stats count by title
| table title
| eval indexes=if(match(title,"^_"),"_*","*")
| rename title as indexes_new]
| eval indexes=if(indexes_orig!=indexes_new,indexes_new, indexes_orig)
| table title indexes
| join indexes max=0 type=inner
[| rest splunk_server=* /services/data/indexes-extended
| fields title frozenTimePeriodInSecs
| rename title as indexes]]
| rename user as Username title as Role indexes as Index
| dedup Index
| eval retentionInDays=frozenTimePeriodInSecs/86400
| table Username Role Index retentionInDaysIf needed you could try to optimise with those splunk_server parts so that auth+user+role stuff will get from your SH side and indexes from your indexer sides.
r. Ismo
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@isoutamo Thanks for your reply but its not returning any results.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
when you are using map on this content you must use $$field$$ instead of $field$.
r. Ismo