Join the Conversation
- Find Answers
- :
- Using Splunk
- :
- Dashboards & Visualizations
- :
- How to visually distinguish dashboard column value...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The objective is to display multiple modifications done by the Submitter, And to show number of modifications, respective filenames and hash names.
Example :
Submitter John did 15 modifications,
3 modification to file app.exe
2 modifications to gap.exe
10 modifications to rap.exe.
So the display should show 15 hash files . And my SPL does the job.
The SPL ends with
| stats values(risk_country) AS extreme_risk_country, list(flagged_threat) AS flagged_threat, list(times_submitted) AS times_submitted, list(md5_count) AS unique_md5, list(meaningful_name) AS file_name, list(md5_value) as md5 by submitter_id
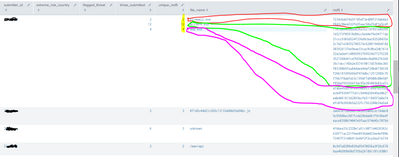
I do see the results, but I am unable to easily eye-ball where the hash file of one filename ends and other one begins. especially when there are lots of hashes. Please check the attachment of the output I am getting. I want to easily see/distinguish where one set of hashes finish for a file and other one starts.
I am looking for suggestions to achieve it in some way to look it visually separate .
Thank you.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This line
| stats sum("attributes.times_submitted") AS times_submitted, dc("attributes.md5") AS md5_count, values("attributes.md5") AS md5_value, values(risk_country) as risk_country, values(flagged_threat) AS flagged_threat by "attributes.meaningful_name", "context_attributes.submitter.id"has effectively collapsed all the unique md5 values by file name (attributes.meaningful_name).
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
My guess is that it is elsewhere in the SPL. For example, how do you calculate md5_count?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
index="secue" sourcetype="sec:json" attributes.meaningful_name!="" | rename "context_attributes.submitter.country" AS country | eval match_risk="Extreme" | lookup riskyNation.csv country_code AS country, Risk AS match_risk OUTPUTNEW Country AS risk_country | fillnull value=" " risk_country | rename "attributes.popular_threat_classification.popular_threat_name{}.value" AS threat_name | lookup flagged_threats.csv threat_name AS threat_name OUTPUTNEW flagged_threat | fillnull value=" " flagged_threat | stats sum("attributes.times_submitted") AS times_submitted, dc("attributes.md5") AS md5_count, values("attributes.md5") AS md5_value, values(risk_country) as risk_country, values(flagged_threat) AS flagged_threat by "attributes.meaningful_name", "context_attributes.submitter.id" | search md5_count > 1 | rename "context_attributes.submitter.id" AS submitter_id | rename "attributes.meaningful_name" AS meaningful_name | stats values(risk_country) AS extreme_risk_country, list(flagged_threat) AS flagged_threat, list(times_submitted) AS times_submitted, list(md5_count) AS unique_md5, list(meaningful_name) AS file_name, list(md5_value) as md5 by submitter_id
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This line
| stats sum("attributes.times_submitted") AS times_submitted, dc("attributes.md5") AS md5_count, values("attributes.md5") AS md5_value, values(risk_country) as risk_country, values(flagged_threat) AS flagged_threat by "attributes.meaningful_name", "context_attributes.submitter.id"has effectively collapsed all the unique md5 values by file name (attributes.meaningful_name).