Are you a member of the Splunk Community?
- Find Answers
- :
- Apps & Add-ons
- :
- All Apps and Add-ons
- :
- ldapsearch error_message=password is mandatory in ...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
ldapsearch error_message=password is mandatory in simple bind
Hi.
I observe a problem with requests to my controller through the application Ldapsearch.
Users (with the role Power) cannot fulfill the request through.
An error occurs while executing the request
External search command 'ldapsearch' returned error code 1. Script output = "error_message=password is mandatory in simple bind ".
See attachment.
I, under the role of administrator (Admin), easily perform ldap requests.
Stanza is configured correctly. The connection test passes.
The account under which requests are made in ldap and integration with AD in attribute worth the value UserAccountControl - DONT_EXPIRE_PASSWORD.
Users with the Power role have been granted application ldapsearch rights
Please, what other suggestions could there be ?

- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Try adding the "list_storage_passwords" capability to the role of users who need to use the ldapsearch commands directly. This allows the users to retrieve the configured passwords for each bind account so that Splunk can make LDAP requests.
I would recommend adding a new role with this capability and adding that role to users who need to be able to use ldapsearch commands, as the "list_storage_passwords" capability will allow them to hit the REST endpoint and view passwords stored in Splunk in cleartext.
The admin role will automatically have this capability, which is why it works.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This solution worked in our environment.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
can you verify common configuration errors using this list:
https://docs.splunk.com/Documentation/SA-LdapSearch/3.0.1/User/UseSA-ldapsearchtotroubleshootproblem...
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
can you double check that credentials have been set in the add-on configuration page:
https://docs.splunk.com/Documentation/SA-LdapSearch/3.0.1/User/ConfiguretheSplunkSupportingAdd-onfor...
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi PavelP
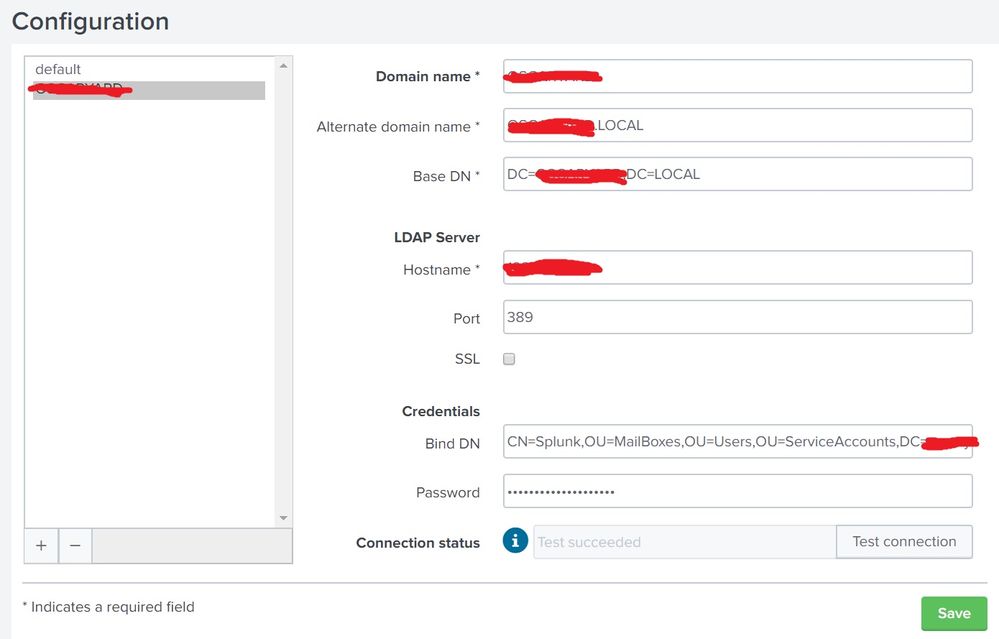
I can check three times if this gives a positive result.
But as I said, the request can be fulfilled only under the role of the Admin.
Above, I attached a screenshot of my configuration.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
PavelP Thanks helped !!
I didn’t look at the page for setting up this application before.
The addition of this admin_all_objects capability helped.
@PavelP Please tell me one request if you know.
I don’t want to create another ticket separately )
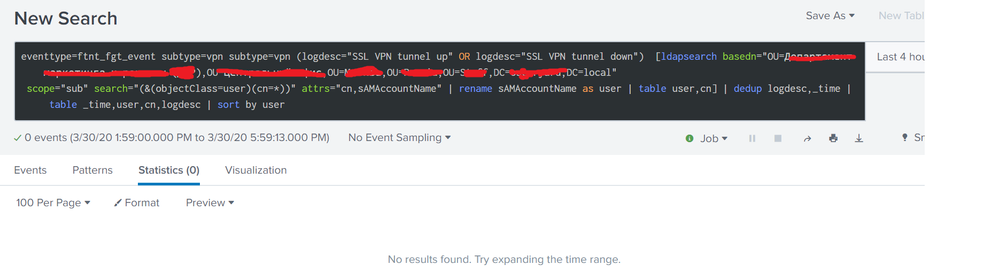
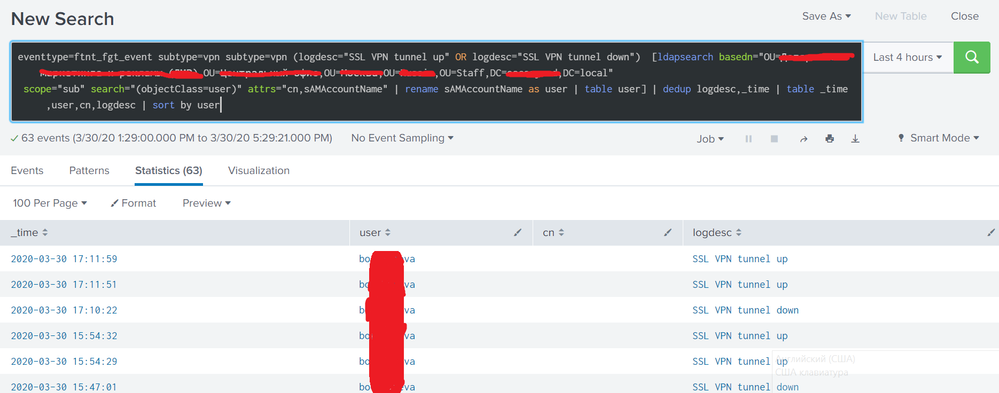
The essence of the request, the first request to pull out users connected via VPN from the fortigate index, in which only the user from a certain department filters out the subquery by ldap.
The output output works out as it should, BUT I still want to output the attribute CN. Full name last name middle name.
Here I can’t understand how to add this attribute to the request to display.
Screenshots in the attachment
Tried to execute the request with I tried to fulfill the request to add the CN attribute to the search, as well as the option attrs="cn,sAMAccountName"
search="(&(objectClass=user)(cn=*))" attrs="cn,sAMAccountName"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
you can first try with ldapsearch CLI tool to get the LDAP query right.
please accept the previous answer/comment as solution (alternatively I can convert my comment to an answer) so everybody can benefit from it.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
have you checked that the user has admin_all_objects capability as mentioned in the article?