- Apps & Add-ons
- :
- All Apps and Add-ons
- :
- All Apps and Add-ons
- :
- Re: Windows TA XmlFixup source transforms not appl...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Windows TA XmlFixup source transforms not applying
Utilizing Splunk_TA_windows 5.0.1, on Splunk 7.1.2 - I have applocker event log inputs defined (with renderXml = true) on various hosts running the Universal Forwarder, with no sourcetype set in the inputs.conf.
The issue is that the TA is not properly setting the expected source for an XmlWinEventLog* sourcetyped event. They remain as they were before the TA upgrade - which is "WinEventLog:Microsoft-Windows-AppLocker/EXE and DLL" instead of the expected "XmlWinEventLog:Microsoft-Windows-AppLocker/EXE and DLL".
It gets more confusing because the TA renames sourcetypes at search time with a props "rename" option, but I was able to verify the sourcetype is indexed correctly by searching using _sourcetype instead and getting the expected results.
On our heavy forwarder, I dug into the TA and found a couple wildcard stanzas that apply transforms which are supposed to change the source and sourcetype:
default\props.conf
[(?::){0}WinEventLog:*]
TRANSFORMS-Fixup = ta-windows-fix-classic-source,ta-windows-fix-sourcetype
[(?::){0}XmlWinEventLog:*]
TRANSFORMS-XmlFixup = ta-windows-fix-xml-source,ta-windows-fix-sourcetype
default\transforms.conf
[ta-windows-fix-classic-source]
DEST_KEY = MetaData:Source
REGEX = (?m)^LogName=(.+?)\s*$
FORMAT = source::WinEventLog:$1
[ta-windows-fix-xml-source]
DEST_KEY = MetaData:Source
REGEX = <Channel>(.+?)<\/Channel>.*
FORMAT = source::XmlWinEventLog:$1
[ta-windows-fix-sourcetype]
SOURCE_KEY = MetaData:Sourcetype
DEST_KEY = MetaData:Sourcetype
REGEX = sourcetype::([^:]*)
FORMAT = sourcetype::$1
However, these don't seem to be matching events properly, in this specific example, an event sourcetyped "XmlWinEventLog:Microsoft-Windows-AppLocker/EXE and DLL".
To test, I added the following stanza in the windows TA local\props.conf on the HF and restarted it:
[XmlWinEventLog:Microsoft-Windows-AppLocker/EXE and DLL]
TRANSFORMS-XmlFixup = ta-windows-fix-xml-source,ta-windows-fix-sourcetype
And I get the expected results - the transforms now apply to that sourcetype, and the correct source of "XmlWinEventLog:Microsoft-Windows-AppLocker/EXE and DLL" is now indexed.
Is this a bug in the TA or my version of Splunk with the "undocumented" sourcetype stanza wildcard method, or have I got something misconfigured?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hey @c.boggs,
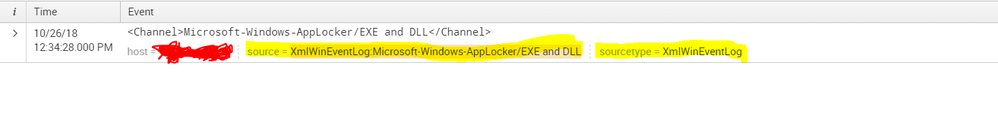
As I didn't have a live event for the same, I verified this using make results on Splunk 7.0.0 Standalone machine, by installing the latest Windows TA-5.0.1
Things did work as expected for me, source converted to XmlWinEventLog:Microsoft-Windows-AppLocker/EXE and DLL while sourcetype to XmlWinEventLog
I don't think there is an issue with TA.
Still a sample event from you can be helpful to crosscheck.
PFA of my sample event got correctly assigned source and sourcetype screenshot.