Join the Conversation
- Find Answers
- :
- Apps & Add-ons
- :
- All Apps and Add-ons
- :
- Technology Add-on for Cisco Secure Access Control ...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Guys,
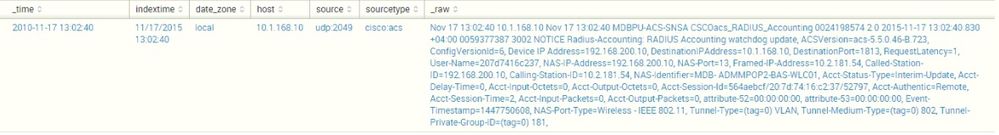
I am facing issue with the _time field. Splunk is not recognizing the time properly, but all other things are working perfectly like _indextime and all.
I am attaching the screenshot for references.
I had even included following things in props.conf file on both the paths etc\system\local & etc\apps\TA_cisco_ios\local, but after doing that, still no luck
[cisco:acs]
# TIME_PREFIX = ^
# TIME_FORMAT = %B %d %H:%M:%S
# MAX_TIMESTAMP_LOOKAHEAD = 19
# SHOULD_LINEMERGE = false
# LINE_BREAKER = ([\r\n]+)(\w{3}\s+\d+\s+\d{2}:\d{2}:\d{2}\s)
# TRUNCATE = 999999
Any solutions to sort this out?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If you are shooting for the first timestamp in that event, then the only problem that you have is that your settings are commented out! So change to this:
[cisco:acs]
TIME_PREFIX = ^
TIME_FORMAT = %B %d %H:%M:%S
MAX_TIMESTAMP_LOOKAHEAD = 19
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If you are shooting for the first timestamp in that event, then the only problem that you have is that your settings are commented out! So change to this:
[cisco:acs]
TIME_PREFIX = ^
TIME_FORMAT = %B %d %H:%M:%S
MAX_TIMESTAMP_LOOKAHEAD = 19
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks Wood !
I didt noticed that at all, lol 🙂 it was a silly mistake 🙂
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hey faizancool85,
I see at least three possible time stamps here, one at the start of the event, another one following directly behind it, and then there is one in the event (after the CSCOacs_RADIUS_Accounting). Which of these would you like to use?
Thanks,
Dave
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Dave,
Thank your for your reply!
I was trying to use _time event.
It was small mistake, i didnt notice that at all. I forget to remove the comment 😞
now its working fine.