Join the Conversation
- Find Answers
- :
- Apps & Add-ons
- :
- All Apps and Add-ons
- :
- Re: Microsoft Azure Add-on for Splunk version conf...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I installed version 3.0.1 of the Microsoft Azure Add-on for Splunk on one of our Heavy Forwarders. I was able to configure and get all the inputs working except "Microsoft Azure Active Directory Sign-ins", "Microsoft Azure Active Directory Users", and "Microsoft Azure Active Directory Audit" (I'm trying to avoid using the EventHub because of the necessary firewall rules, etc.). All of our Splunk servers are Linux and we have version 8.0.5 installed.
The error I'm seeing is:
2020-08-10 16:25:11,467 ERROR pid=23994 tid=MainThread file=base_modinput.py:log_error:309 | Get error when collecting events.
Traceback (most recent call last):
File "/opt/splunk/etc/apps/TA-MS-AAD/bin/ta_ms_aad/aob_py3/modinput_wrapper/base_modinput.py", line 128, in stream_events
self.collect_events(ew)
File "/opt/splunk/etc/apps/TA-MS-AAD/bin/MS_AAD_signins.py", line 88, in collect_events
input_module.collect_events(self, ew)
File "/opt/splunk/etc/apps/TA-MS-AAD/bin/input_module_MS_AAD_signins.py", line 85, in collect_events
sign_in_response = azutils.get_items_batch(helper, access_token, url)
File "/opt/splunk/etc/apps/TA-MS-AAD/bin/ta_azure_utils/utils.py", line 55, in get_items_batch
raise e
File "/opt/splunk/etc/apps/TA-MS-AAD/bin/ta_azure_utils/utils.py", line 49, in get_items_batch
r.raise_for_status()
File "/opt/splunk/etc/apps/TA-MS-AAD/bin/ta_ms_aad/aob_py3/requests/models.py", line 940, in raise_for_status
raise HTTPError(http_error_msg, response=self)
requests.exceptions.HTTPError: 403 Client Error: Forbidden for url: https://graph.microsoft.com/beta/auditLogs/signIns?$orderby=createdDateTime&$filter=createdDateTime+gt+2020-08-09T16:25:10.822417Z+and+createdDateTime+le+2020-08-10T21:18:11.232754ZI assume this means the necessary permissions are not in place in Azure. Our Azure admin followed the "Setup an Azure AD Application Registration" documentation built-in to the app ( which is really nice btw ). He doublechecked and he did everything in the instructions. Any ideas on what we might be missing? I looked at the troubleshooting search and didn't come across anything that seemed to spell out what the problem was (beyond what the error above indicates).
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Funny. I literally ran into this with another customer again today. There are 2 issues that I've found cause the 403 error:
#1 - you MUST have Premium P1 or P2 licensing for this to work. You can access the Sign-in logs via Azure AD portal without it, but not via api: https://github.com/microsoftgraph/microsoft-graph-docs/issues/10987
#2 - The specific permission that's not documented in the MS rights and is required is Diretory.Read.All (Application). Without this, I've found it to be intermittent (and in some cases, just never works).
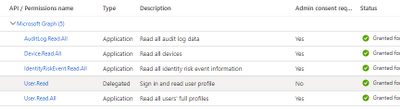
The following set of permissions allow me to collect Azure AD, O365, and Graph API Security logs all with one AppID:
Microsoft Graph:
AuditLog.Read.All (Application)
Diretory.Read.All (Application)
SecurityEvents.Read.All (Application)
User.Read (Delegated) <--- this is set by default
User.Read.All (Application)
Office 365 Management APIs:
ActivityFeed.Read (Application)
ActivityFeed.ReadDlp (Application)
ServiceHealth.Read (Application)
Thanks,
Gord T.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Did anyone solve this? We have given the user the rights as documented, but still are getting the Client Forbidden 403 error... as below.. all the other log collections are function without ERROR, but this one just never works...
requests.exceptions.HTTPError: 403 Client Error: Forbidden for url: https://graph.microsoft.com/v1.0/auditLogs/signIns?$orderby=createdDateTime&$filter=createdDateTime+gt+2021-03-25T15:46:06.943832Z+and+createdDateTime+le+2021-03-26T19:39:07.304625Z
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Funny. I literally ran into this with another customer again today. There are 2 issues that I've found cause the 403 error:
#1 - you MUST have Premium P1 or P2 licensing for this to work. You can access the Sign-in logs via Azure AD portal without it, but not via api: https://github.com/microsoftgraph/microsoft-graph-docs/issues/10987
#2 - The specific permission that's not documented in the MS rights and is required is Diretory.Read.All (Application). Without this, I've found it to be intermittent (and in some cases, just never works).
The following set of permissions allow me to collect Azure AD, O365, and Graph API Security logs all with one AppID:
Microsoft Graph:
AuditLog.Read.All (Application)
Diretory.Read.All (Application)
SecurityEvents.Read.All (Application)
User.Read (Delegated) <--- this is set by default
User.Read.All (Application)
Office 365 Management APIs:
ActivityFeed.Read (Application)
ActivityFeed.ReadDlp (Application)
ServiceHealth.Read (Application)
Thanks,
Gord T.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
For us, it turned out to be a license issue. I have no idea why this isn't the first thing Microsoft support checked. Once we upgraded our license we were able to pull back sign-in logs.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We are encountering the same issue. Did you ever figure out the correct perms or what the issue is?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We have a case open with Microsoft. We have the permissions specified here set accordingly. They asked us for a fiddler trace and while I was working on that, I was interrupted by an audit evidence request. When we get it sorted out I will post an update.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hey there, did you ever resolve?
I've posted similarly in another thread with the same issue.
I've setup the permissions per http://bit.ly/Splunk_Azure_Permissions. Specifically:
| Microsoft Azure Active Directory Sign-ins | Microsoft Graph | (Application) AuditLog.Read.All - Read all audit log data |
I have tried with two tenancies both resulting the same 403.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I believe the key permission that you're missing is Directory.Read.All (Application).
I consolidated my O365, AzureAD, and GraphAPI permissions into a single appID with the following permissions which work fine:
Microsoft Graph:
AuditLog.Read.All (Application)
Diretory.Read.All (Application)
SecurityEvents.Read.All (Application)
User.Read (Delegated) <--- this is set by default
User.Read.All (Application)
Office 365 Management APIs:
ActivityFeed.Read (Application)
ActivityFeed.ReadDlp (Application)
ServiceHealth.Read (Application)
Hope this helps!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We have the same issue with the same error. Ours works periodically, then stops, then starts up again.
Haven't had a chance to open a case with Microsoft yet, so am curious what they come up with.