- Apps & Add-ons
- :
- All Apps and Add-ons
- :
- All Apps and Add-ons
- :
- Help Needed: SA-cim_validator Returns No Results
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Help Needed: SA-cim_validator Returns No Results
Hello Splunk Community,
I'm encountering an issue with the SA-cim_validator add-on where it's returning no results, and I'm hoping someone here can help me troubleshoot this further.
Here's what I've done so far:
- Confirmed that the app has read access for all users and write access for admin roles.
- Checked that the configuration files are correctly set up.
- Splunk Common Information Model (Splunk_SA_CIM) is installed and up to date.
- Verified that the indexes and sourcetypes specified in the queries are present and contain data.
- Reviewed time ranges to include periods with log generation.
- Ensured that data models are accelerated as needed.
- Looked through Splunk's internal logs for any errors related to the SA-cim_validator but found nothing.
Despite these steps, every time I run a search query within the CIM Validator, such as index=fortigate sourcetype=fortigate_utm, it yields no results, regardless of the indexes or targeted data model or search parameters I use.
Does anyone have any insights or suggestions on what else I can check or any known issues with the add-on? Any assistance would be greatly appreciated!
Thank you,
Alex_Mics
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Actually, it may be that something is wrong with your CIM Validator. Even if I try to search a non-existent index, it still populates the counters at the top and has rows of "no extracted values found"
Which version of Cim Validator are you using? Perhaps you could try backing up the current cim validator app, then re-installing it.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It sounds like you are doing everything right. I freshly installed the CIM Validator v 1.8.2 on Splunk Enterprise v9.2.0 with the Splunk CIM app v5.3.1, then without configuring any of these apps I entered "index=_internal" into the search bar of the CIM Validator app dashboard and then I could see results.
It is very strange that you are able to retrieve logs from regular Splunk searches, but then get no results when you copy the search query into the CIM Validator and set the time range to be equivalent.
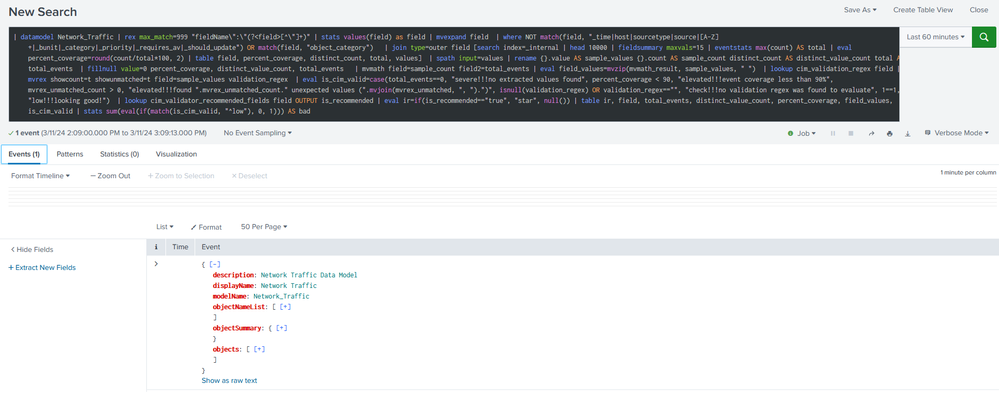
At the very bottom of the CIM Validator dashboard, there is a table labeled "Events". You can click the magnifying glass on this table and it will open a search containing your search query followed by "| head 10000". As this is a very straightforward search, you should be able to see events in this table once you enter them into the "Search" input of the CIM dashboard.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for replying Marnall.
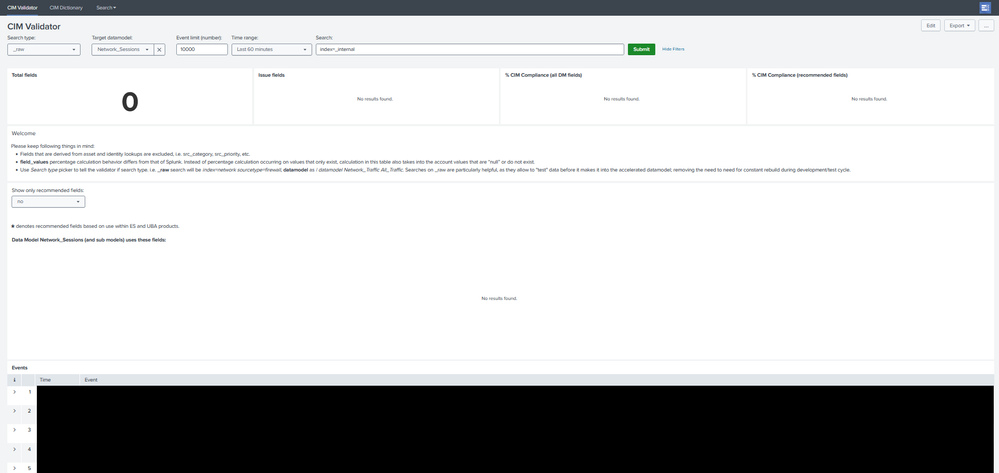
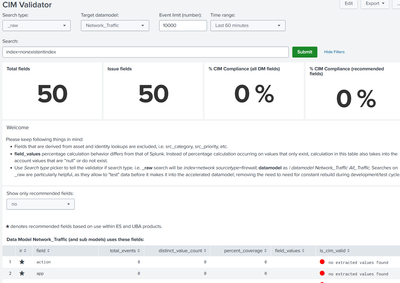
It is indeed very strange that the CIM Validator does not return any results. Especially since as you mentioned, at the bottom of the page there is a table labelled "Events" that does return results.
I do not recall if this issue was present last week, but trying to click on the "Search type" drop down menu and clicking on "datamodel" no longer saves that selection. It is permanently stuck on "_raw".
Clicking on all the magnifying glasses of each search, the results are almost always the same:
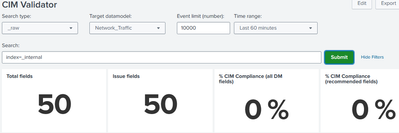
- "Total fields" always returns a count of zero.
- The rest all return the data model that I have selected.
I've added several screenshots to showing what I see. I hope there will be more suggestions for troubleshooting.