- Apps & Add-ons
- :
- All Apps and Add-ons
- :
- All Apps and Add-ons
- :
- Re: FireEye App for Splunk Enterprise v3: Why is t...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
FireEye App for Splunk Enterprise v3: Why is the app not displaying any data in the dashboard and event view?
I have installed FireEye App for Splunk Enterprise v3 in Splunk 6.x. FireEye EX 7.x sends XML syslog to Splunk.
I set the sourcetype as "fireeye" in Splunk, I can successfully search the fireeye log by sourcetype=fireeye". However the FIreEye App 3.0 does not show any data in dashboard and in event view.
the log format received as attached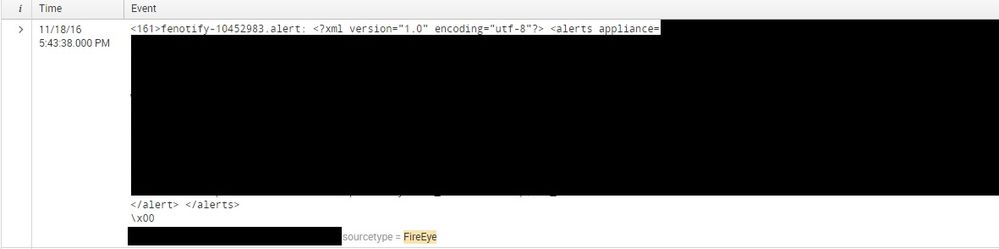
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Please see the valid sourcetypes section in the Details page below. For this format, you need to use fe_xml_syslog. It may be best to start simple (ex: fe_cef_syslog) though and then go to a more robust format.
https://splunkbase.splunk.com/app/1845/#/details
Pasted below for your convenience:
Sourcetypes
Supported protocols and corresponding sourcetypes are:
Protocol/format Sourcetype
1) JSON over HTTPS fe_json
2) XML over HTTPS fe_xml
3) CEF over SYSLOG - TCP fe_cef_syslog
4) CEF over SYSLOG - UDP fe_cef_syslog
5) XML over SYSLOG - TCP fe_xml_syslog
6) XML over SYSLOG - UDP fe_xml_syslog
7) JSON over SYSLOG - TCP fe_json_syslog
8) JSON over SYSLOG - UDP fe_json_syslog
9) CSV over SYSLOG - TCP fe_csv_syslog
10) CSV over SYSLOG - UDP fe_csv_syslog
HX Endpoint Appliance hx_cef_syslog
Threat Analytics Platform (TAP) fe_tap_json
Email Threat Prevention (ETP) fe_etp
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
And I would like to highlight to you that the statistic (e.g. Total Malicious Email, Attachement) are not correct. This is because fireeye sends two or more events for single email if the email attachment is zipped. It can't simply count the user or hash. The logic may be complex.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I modify your extraction "fe_xml_syslog : EXTRACT-mail_suser_duser_for_fireeye". The domain field is removed from your extraction, then it works. the raw log does not have domain field.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
after change sourcetype=fe_xml_syslog, some dashboards (e.g. serverity, malware)
can shows content. However, some dashboards (e.g. senders, recipients) show no content. The fireeye app cannot parse the xml log to extracts some fields.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
So you are parsing EX events. We would need to set up a VTC to see why it is not parsing. Feel free to send an email via the app (Help -> Send Feedback) so we can set one up.
Alternatively, did you try switching to sourcetype fe_cef_syslog and changing the FEYE appliances to use syslog and CEF to see if that meets your needs?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Do you mean that I need manually set the source type as "fe_xml_syslog" in the Splunk's Data Inputs setting page?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Instead of setting it to fireeye as you mentioned before. Set it to fe_xml_syslog, then let us know if it works.
