Are you a member of the Splunk Community?
- Find Answers
- :
- Apps & Add-ons
- :
- All Apps and Add-ons
- :
- Re: CIM is not getting validated after Splunk upgr...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
CIM is not getting validated after Splunk upgrade from 6.3 to 6.4.1
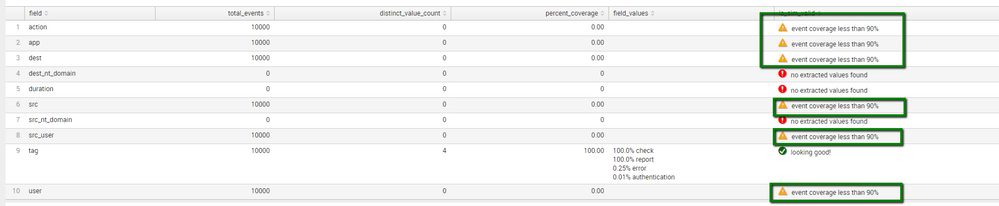
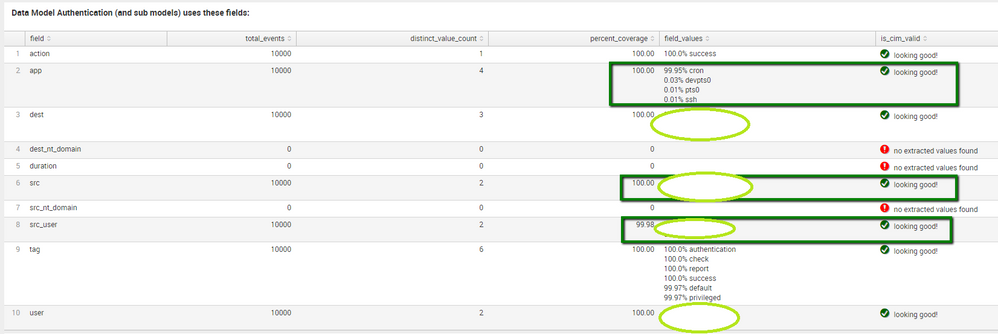
I have upgraded Splunk from 6.3 to 6.4.1 and I found CIM validation is not looking good (Refer below screen shot). It is showing event coverage less than 90 % and CIM is not validated. However, before upgrading, it was well and good for the corresponding fields (Refer 2nd screen shot below).
I am not sure where went wrong and why CIM is not validating the events. If anyone can please help me out, it would be of great help. Thanks in advance.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is caused by Enterprise Security's app import regex: https://github.com/doksu/splunk_auditd/wiki/Release-Notes#known-issues
I would suggest creating a local app_regex in the Enterprise Security app:
SplunkEnterpriseSecuritySuite/local/inputs.conf:
[app_imports_update://update_es]
app_regex = (appsbrowser)|(search)|([ST]A-.*)|(Splunk_[ST]A_.*)|(DA-ESS-.*)|(Splunk_DA-ESS_.*)|(TA_.*)
disabled = 0
Please see https://github.com/doksu/splunk_auditd/issues/11 for more discussion about the issue.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Which version of the TA_linux-auditd app is installed?
Which version of the CIM app is installed?
If you run the search: eventtype=auditd_events in "Smart Mode", do you see the normal list of fields on the left-hand side?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Which version of the TA_linux-auditd app is installed?
Current Application: Linux Auditd
App Version
2.0.2
Which version of the CIM app is installed?
Target CIM version: 4.3.1
Current Application: SA-cim_validator
App Version
1.0
App Build
1
If you run the search: eventtype=auditd_events in "Smart Mode", do you see the normal list of fields on the left-hand side?
Yes, can see only on Search & Reporting app and Linux_auditd app. But there is no search result in CIM app and ES app.
Please help.